Intel microcode security update (CROSSTalk)
A new security update is available for Intel microcode, accompanied by a Xen update to handle the new microcode.
Updates are available for XCP-ng 8.0 and 8.1.
To update, follow this guide. Join the discussion on our community forum.
Reboot after updating.
Related: https://support.citrix.com/article/CTX275165
CVE ID: CVE-2020-0543.
CROSSTalk vulnerabilities (SRBDS)
As usual, this new Intel CPU vulnerability got a marketing codename from the researchers that uncovered it: CROSSTalk. Intel named it Special Register Buffer Data Sampling (SRBDS).
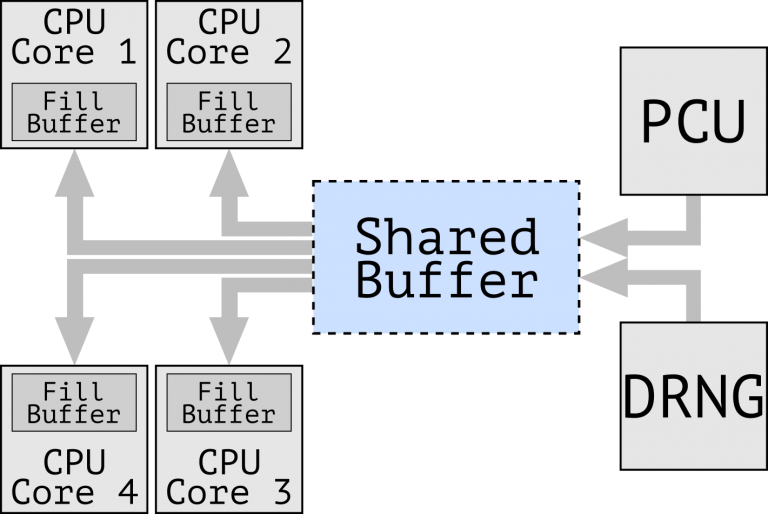
This is once again related to speculative execution, but there's something new: data leaks between physical cores, using data that transits through a shared buffer. Among the data that can be leaked are results from the random number generator, that are heavily used in cryptography.
Intel microcode update
The updated microcode mitigates the issue for the CPU models that are still supported by Intel.
The performance impact of the fix is so important that Intel chose not to protect all instructions that use that shared buffer, but only the ones that they considered posing a high risk: RDRAND, RDSEED and EGETKEY. This can have a significant impact on the performance of workloads that make a heavy use of those instructions.
What CPUs are vulnerable, what CPUs get new microcode
Refer to this matrix of all models and vulnerabilities.
Column "Special Register Buffer Data Sampling" tells if your CPU is affected.
If the "Microarchitecture" column contains "RETIRED" for your CPU family, then there are no microcode updates for those.
No updates are available from Intel for the affected IvyBridge CPUs.
Xen update
Xen has been updated at the same time as the microcodes:
- displays
SRBDS_CTRLin/var/log/xen/hypervisor.logwhen the microcode supports the new feature. - displays
SRB_LOCK+(=secure) if the feature is enabled by Xen, elseSRB_LOCK-(=fast). Default isSRB_LOCK+. - allows to control the feature via a boot option. See Xen's documentation for the
spec-ctrlboot parameter, which allows to control speculative execution mitigations. Example: usespec-ctrl=no-srb-lockto specifically disable the new SRB_LOCK mitigation.
Kernel update
The linux kernel is also updated to reduce the performance impact of the new microcode.
What to do
Update following the usual guide, reboot the hosts, evaluate the performance impact if you are affected and decide between safety and performance.
If you are using affected hardware for which no new microcode is available (IvyBridge), read Xen's advisory MITIGATION section. This is only possible in XCP-ng 8.1 at the moment.