RETBleed security patch
You probably heard of it: there's a new CPU vulnerability in town, affecting various CPUs, both Intel and AMD (and likely even non-x86 architectures: it's a pretty "wide" problem). So here is the software mitigation for it, directly added inside Xen hypervisor.
Summary
RETbleed is a speculative execution attack on x86-64 processors, including some recent Intel and AMD chips. You can read the original announcement from Computer Security Group at this address: https://comsec.ethz.ch/research/microarch/retbleed/
Despite sounding similar to previous speculative execution attacks targeting indirect jumps (the whole Spectre family), RETbleed exploits return instructions. And it's a big deal, since it defeats the existing Spectre-like mitigations in place. Not convinced? See this demo:
In terms of affected hardware, here is a list of tested CPUs against it:
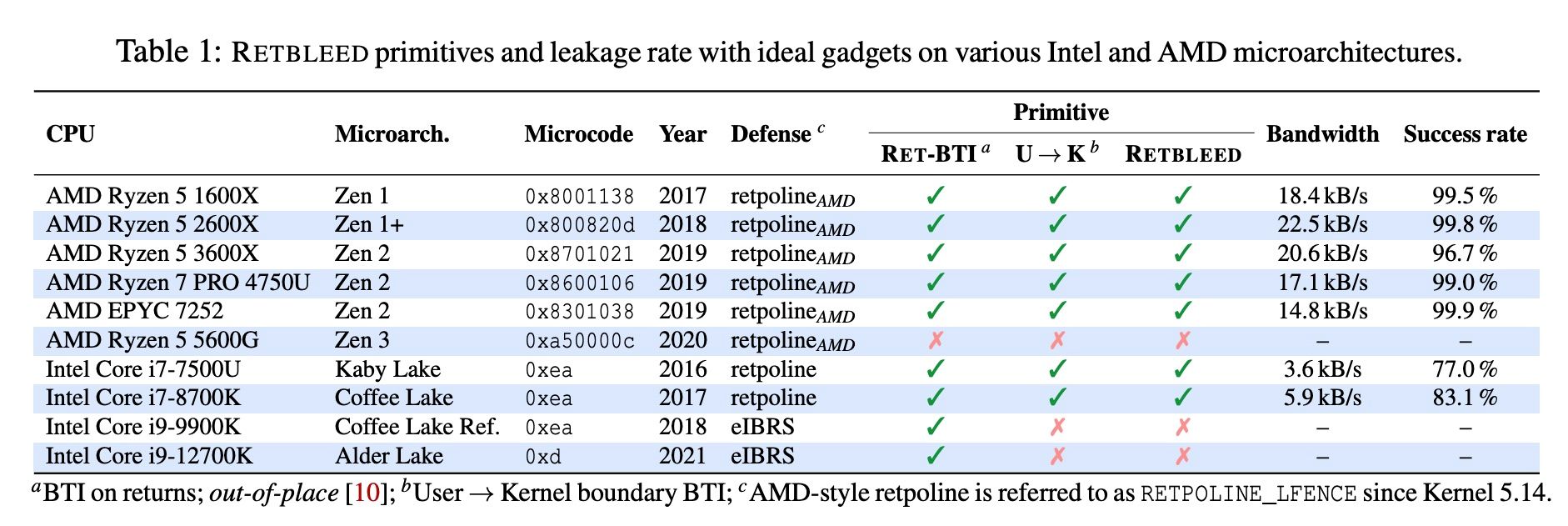
Impact
Due to this hardware security flaw, an attacker might be able to infer the contents of arbitrary host memory, including memory assigned to other guests.
References
- Xen Project's Security Advisory: XSA-407
- Computer Security Group original paper
- Citrix Hypervisor's Security Bulletin
- CVE-2022-29900 for AMD and CVE-2022-29901 for Intel




