XCP-ng 8.3 Alpha
It's time to discover what's beyond our existing LTS release. To the moon and beyond! 🚀
Key points
Before doing a deep dive on all the details, we'll give you some key points to understand what will be our XCP-ng 8.3 version, and more than that: what it won't be!
🚫 This is not an LTS, I repeat, not an LTS
This new 8.3 won't be an LTS. If you want long term support and stability (mostly only security fixes), please stay on XCP-ng 8.2.
However, 8.3 is a great opportunity for people who want to play with more cutting edge features. In fact, even if this Alpha 8.3 is already bringing various modifications, it's just a start! Our target: adding exciting features well after the "official" release. In other words, new stuff will still come after the alpha, beta, release candidate (if any) and the "actual" release.
💪 Teamwork
Let's discuss some important context to understand more what this alpha is about: it's based on a "preview" release of "Citrix Hypervisor 8 Cloud" or whatever it's future name, "XenServer 8 Cloud".
Until now, we always started to build XCP-ng on top of a Citrix "production ready release", explaining the gap between a Citrix release date and ours. Indeed, we usually spent some time to add our components, reviewed all the changes (even reporting bugs to Citrix!) and in the end finally got our own alpha/beta/release cycle.
It may be useful to explain why this is an important difference. It's a good thing because we can manage to provide feedback to Citrix before their own release lands in production, increasing the value of our collaboration. Fixing common bugs together is truly a great step forward, and we wanted to thank the XenServer dev team for their great help and our increased teamwork in the last months. We are stronger together!
🧊 The tip of the iceberg
Although many components were updated under the hood, there aren't so many visible new features - yet. This platform is in fact a great basis for the next big changes. We were pretty conservative for the LTS, and I think everyone enjoyed our huge investment and commitment to provide a truly stable experience despite monthly security (or minor fixes) updates.
For this 8.3, we also want to keep our good track record, but we'll push for bigger changes, and obviously, we'll be less conservative on our choices to push new or updated components!
✅ Alpha but not explosive
So yes, this is an alpha. It means this release will evolve a lot before the final "official" availability. However, the system is pretty stable and all the internal QA tests were executed successfully before we made this alpha release.
Installation and upgrade
As usual, there's 2 ways to get 8.3 running on your machine: fresh install or upgrade from a previous XCP-ng version.
💿 Install
- You can download the ISO here: https://updates.xcp-ng.org/isos/8.3/xcp-ng-8.3.0-alpha2.iso
- For the netinstall version: https://updates.xcp-ng.org/isos/8.3/xcp-ng-8.3.0-alpha2-netinstall.iso
The installation is exactly the same as from our documentation: https://xcp-ng.org/docs/install.html
🔼 Upgrade
Only upgrades using the installation ISO are supported for now. Whether yum-style upgrade will be supported later is still being pondered. For now just insert the ISO, it will detect older versions of XCP-ng and then follow instructions.
You can always rollback later in case something is wrong.

What's new in XCP-ng 8.3
Let's break down the changes in multiple categories:
- 🖥️ Visible changes: things that will be directly visible when installing/using XCP-ng.
- ✨ New features: not "directly" visible on screen but can be used with Xen Orchestra for example.
- 🛠️ Under the hood: invisible but however important changes
We will have a dedicated section for the "🔮 Future work", which is pretty big for this 8.3 release.
🖥️ New theme
Since we updated our identity, this release is an opportunity to match it on the XCP-ng level. You now have a new install splash screen (BIOS mode):
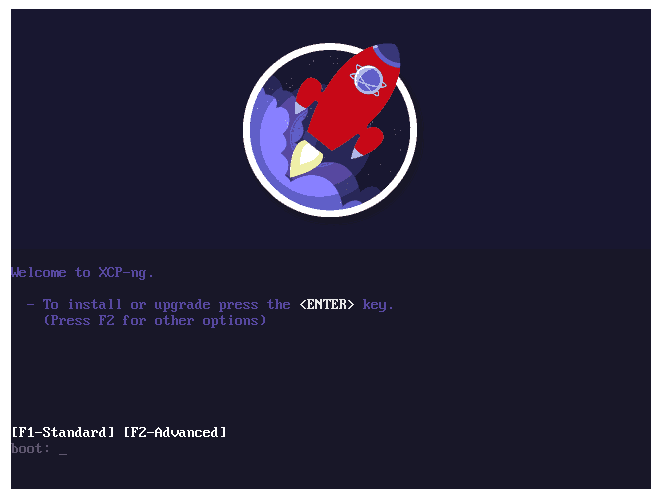
A new starting and shutdown screen:

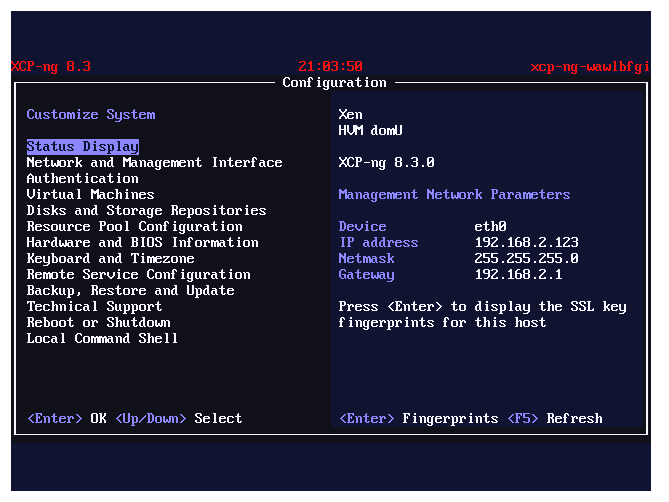
And the xsconsole utility:
And finally, a new prompt theme:
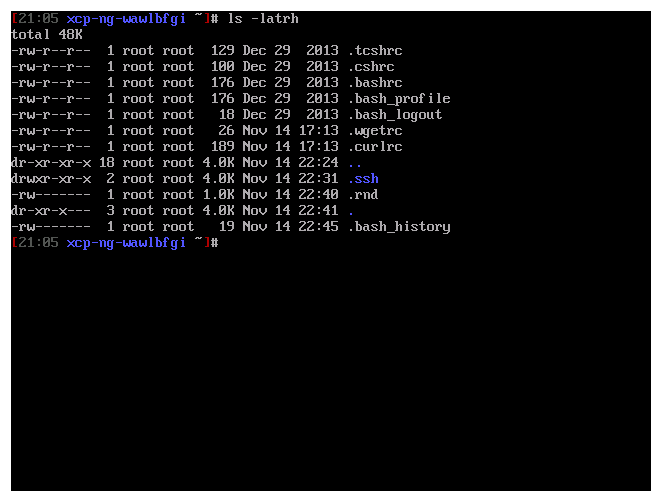
Entirely aligned with XO Lite colors (see below), we are creating a real coherence: you are sure to know where you are and what tools you use!
🖥️ XO Lite integration
XO Lite is now directly embedded in your XCP-ng! Going to your host HTTPS URL will directly show you this now:
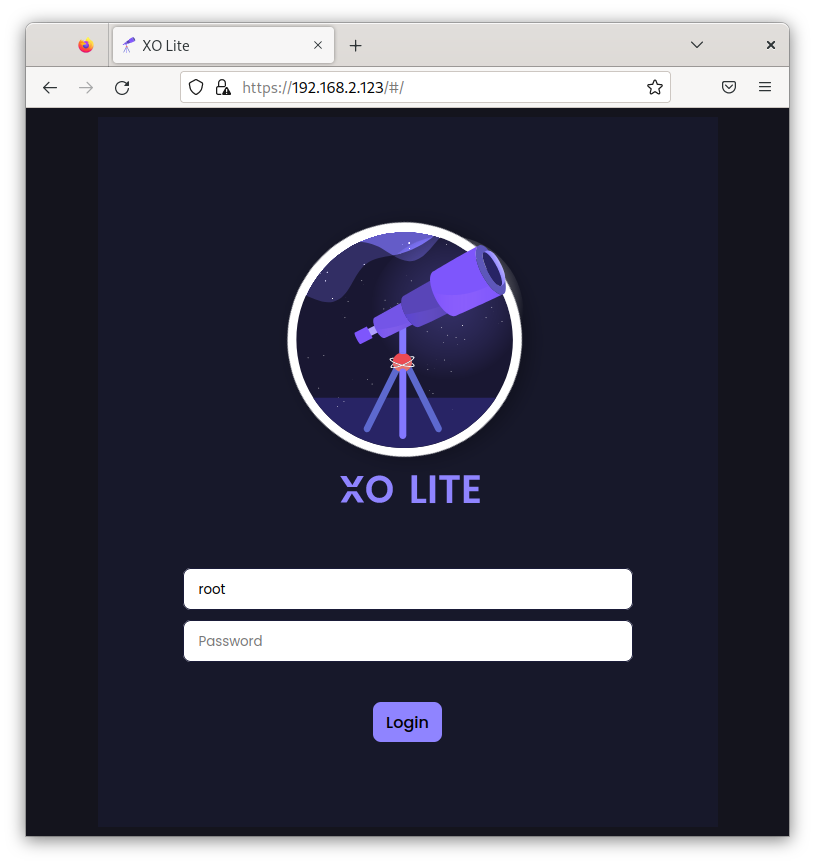
The current embedded version is providing:
- Tree view with pool, hosts and VMs
- VM consoles from the tree view
- Dashboard with global info about infra and stats
- List of all VMs with prototype of advanced filters
- Internationalization (English, French for now)
- Dark mode/Light mode
We'll keep sending updates at least every month, and there's nothing to do on your side, since the JS is loaded directly from the Internet! Stay tuned on Xen Orchestra Blog on new XO Lite updates.
✨ Better Intel NUC support
Thanks to various contributions from the community (👋 Andrew), we managed to get NUC 10 and 11 running on XCP-ng 8.3 without any manual tinkering. The main issue was a blank screen on boot (technical explanation and bug report here). In short, it was fixed by backporting the change to the current Dom0 kernel.

But that's not it! Those NUCs have 2.5Gb ports. And another good news:
✨ 2.5Gb NIC support
We added support for some popular 2.5Gb NICs. With the igc and r8125 drivers, we cover both Intel i225 (including close variants) and also the RTL8125 family from Realtek. This means your Intel NUC with 2.5Gb NIC will work out-of-the-box!
Also, we updated the Intel e1000e driver (for 1Gb NICs), but this version is solving some issues with the previous existing driver.
✨ Installer updated
Another great news on that front: since we increased our collaboration with Citrix, and pushing for IPv6, they finally decided to put the code on a public Github repository. We can now contribute directly and send our patches "upstream" 🥳
There are still some pull requests in review (including IPv6 support during the installation!), but it's a very good thing. It basically means more work done together with the XenServer team and pushing faster improvements.
✨ Host evacuate network selection
This one is a direct contribution in the XAPI toolstack by us, Vates. We modified the code to allow an extra parameter to be specified when you evacuate a host ("evacuate" means: "please migrate off ALL the VMs on this host to another pool member").
This extra parameter will target a network to live migrate the VMs. Maybe you don't want to do that on the management network? It's already available in Xen Orchestra by the way.
✨ VM snapshot with disk exclusion
This feature has also been requested for a long time. We wanted to make a call to the API with VM.snapshot, but excluding some disks, like a raw drive for example, or a very big disk irrelevant to the backup without using space for a snapshot.
Thanks to our contribution in the API, this capability is now available, and… already working in your current stable version of Xen Orchestra!
🛠️ varstored replacing uefistored
Long story short: these two components are functionally identical but using two different implementations, one made originally by Citrix but closed source (varstored) and the other wrote by Vates (uefistored) so we can do also support Secure Boot.
Frankly, it took us some efforts to implement our own version, but a year later, Citrix decided to open source it 🥳 In order to avoid duplicating our efforts, we decided to consider their version the new upstream. This -however- introduces some slight changes regarding Secure Boot support:
- You need to run
secureboot-certs installto install the UEFI certificates to the pool, even if you are upgrading from an XCP-ng that already had certificates installed. We are considering bundling the default certificates with XCP-ng directly so that this manual step can be avoided. - After this, new VMs, when starting for the first time, will automatically get the certificates and be ready to handle Secure Boot.
- Other VMs will require an extra step, on the host:
varstore-sb-state $VM_UUID user.
uefistored, a VM starting with Secure Boot enabled on varstored will still accept to boot even if the Secure Boot certificates are missing from its NVRAM. Which means you might believe that Secure Boot is enforced when it actually isn't.There's still some rough edges in this alpha, but we hope to get everything sorted quickly!
🛠️ TLS check between hosts and clients
Citrix added a TLS certificate verification between clients inside the pool, for all members. This feature is a good step to increase security. You can enable it with:
xe pool-enable-tls-verificationHowever, it's not tested yet.
🛠️ Many other things
In fact, we just listed the major changes, because there's so many small changes that it was impossible to list them all.
🪦 Deprecated or removed features
He's dead Jim!
Here is a small list of features we decided to remove or to deprecate.
- DMC (Dynamic Memory control): in fact, this first feature isn't removed. Let's say "barely saved from removal", because XenServer simply nuked it. We decided to keep it enabled because we know that there are users who depend on it, despite known issues. However, we advise not to use it unless you can't really do without it. And don't set the dynamic min limit too low, unless you want VMs to crash when the hypervisor will tell them to give back RAM that their actually need. We might have some R&D work to rewrite it correctly in the future.
- Legacy partition layout: well, it's been deprecated since 2015 in XenServer, we thought it was time to follow Citrix and to say goodbye to it. We already documented the way to upgrade from the legacy layout.
- AMD MxGPU: Unfortunately, AMD stopped supporting the drivers for MxGPU (not just for XenServer: for anyone, as far as we understand it). They might still work for now, but when the Linux kernel in dom0 will be updated this will stop. Luckily, we started to work on some… alternatives. Stay tuned in that area!
- XCP-ng AD integration: well, again it's not really a removal. Citrix replaced the component used for it (
winbindinstead ofpbis). However, the script handling the transition is kept proprietary by Citrix, which means it's likely that an existing setup would break after an upgrade and need to be done again. In any case, we have never been fans of this way to leverage Active Directory directly inside XCP-ng. We strongly advise to rely on Xen Orchestra to do your user management (which is AD and OpenLDAP compatible) and leave your host far from this.
🔮 Future work
As we said in the intro, this alpha, and more generally this 8.3 release is meant to lay the foundation of many future changes. Having a non-LTS release (in addition to it) opens up a lot of great opportunities. Let's explore some of them!
💿 Nightly builds for our ISO
We worked hard to improve our ISO generation system. We'll be able to -soon- generate a fresh ISO every night or every week, so we can deliver new features faster (like in the installer for example). Or even new drivers! Reducing the cycle between a contribution (external, internal or by Citrix) and it's availability via a fresh ISO is a promising change for our virtualization stack!
6️⃣ IPv6 support for management
We announced the original contribution a while ago, but we are ready to include it into XCP-ng 8.3. As stated earlier in this blog post, we are mostly waiting for inclusion upstream (in the installer repository). It now depends on how fast the XenServer team will do the review.
🔑 vTPM support (Windows 11)
This feature is eagerly awaited by Windows 11 users, because a TPM is mandatory to boot this OS without any tinkering. This effort is supervised and done by the XenServer team. We are monitoring the progress and we think it's not far from being ready. Stay tuned!
🔒 Port 80 removal
There's a work in progress from the XenServer team to remove everything that's not using an encrypted channel. However, there's still some operations relying on a plain connection, and this should be fixed in the next few months.
🛡️ Secure boot improvements
It would be great to have default certificates installed by default, with the ability to override them. Also, avoiding a false sense of security by refusing to boot if Secure Boot is on but VM certificates are missing or corrupted, rather than silently booting without enforcing it.
🏗️ Many other things!
There are also things coming on the longer run, thanks to your improved upstream collaboration. Our roadmap contains realistic targets like LACP support in the installer, xen.efi for iPXE boot in UEFI, network install fetching automatically the latest updates, memtest86+ inclusion for both BIOS and UEFI mode, better update management and the list goes on…
The door is also open for major Xen version updates, kernel updates and even platform updates, but this is another story for a future blog post 😉