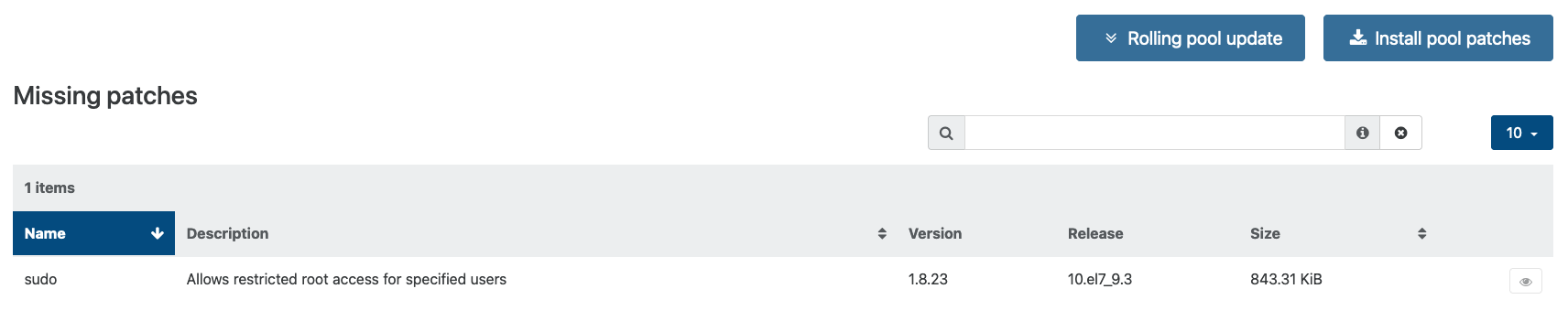
New patch - sudo
-
As far as i know, there is no need to restart the server when updating only sudo.
This update covers the recent security flaw: CVE-2023-22809.
A post will come soon in the update topic about it.
-
@gduperrey My host asked for a reboot yesterday after patching IIRC but I could be wrong.
-
XCP-ng doesn't tell XO whether an update deserves a reboot or not, so XO always says you need to reboot after an update.
In practice, some updates don't require it, but as we usually group updates to reduce your maintenance overhead, most of the time when you see an update for a supported release of XCP-ng, a reboot is needed. For details about updates, you've got the blog: https://xcp-ng.org/blog/tag/update/.
For XCP-ng 8.3, as this is a development release, the above doesn't apply: no blog, and just an announcement in the dedicated thread.
-
So, due a misunderstanding, the sudo update for XCP-ng 8.2 was released before the announcement was ready.
We'll post it soon and it will say no reboot is required for this update.
-
Here's the announcement: https://xcp-ng.org/blog/2023/01/31/january-2023-security-update/
-
@eoin said in New patch - sudo:
@Darkbeldin Oh dear.... okay. Is every patch requiring reboot? If not, are there any ways to figure out if a patch needs reboot or not in XOA?
Just wanted to point out that you should always be prepped to reboot a host periodically, this is true for any hypervisor, it's not a good idea to not patch and just leave it running 24/7, especially in an environment where security matters.
Good thing is reboots of XCP-ng hosts don't really take that long.
-
@planedrop said in New patch - sudo:
@eoin said in New patch - sudo:
@Darkbeldin Oh dear.... okay. Is every patch requiring reboot? If not, are there any ways to figure out if a patch needs reboot or not in XOA?
Just wanted to point out that you should always be prepped to reboot a host periodically, this is true for any hypervisor, it's not a good idea to not patch and just leave it running 24/7, especially in an environment where security matters.
Good thing is reboots of XCP-ng hosts don't really take that long.
While this is also what I'm used to, I have always wondered why it is advertised that no host reboots are required for patches, yet every update requires a patch:
https://xcp-ng.com/pricing.html under "Live Patching":Enables administrators to patch hypervisors without needing to migrate, shut down or suspend VMs (no host reboots required)
-
@NielsH Hmmmm good point, I guess if we are being technical you CAN patch them and a reboot isn't REQUIRED even though it's recommended.
I'd argue, with a security patch, though this could vary greatly from patch to patch, you'd be better off installing it and not rebooting than waiting until you can reboot to install it. If that makes any sense.
-
@planedrop I agree, host reboot is required periodically. If there are only a handful VMs running in a pool, no worries. But in production system, running almost 200 VMs - that's a different story. And literally only one patch needs to be applied, not showing whether reboot is required or not in XOA. At least, I'd like to see if the patch requires reboot or not if possible.
-
@eoin Yeah I do hear you here, I run a setup in prod with 15 VMs, not 200 but of those 15 several are hyper critical and very resource intensive.
Anyway, I think it would be nice to know on a per update basis if it's actually required or not, however I think in general it's best to reboot even if the reboot isn't strictly a requirement.
The other option of course is more hosts, and do a rolling pool update with VMs migrating back and forth, it's a great feature (not one I use in prod since 15 VMs isn't that huge of a deal to do manually) and helps with this exact issue, costs more though too of course!
-
I'd argue, with a security patch, though this could vary greatly from patch to patch, you'd be better off installing it and not rebooting than waiting until you can reboot to install it. If that makes any sense.
Better not install security patches that require a reboot without rebooting. All you create is a discrepancy between what resides in memory and what is on disk, and in rare cases things may break, for no added security.
While this is also what I'm used to, I have always wondered why it is advertised that no host reboots are required for patches, yet every update requires a patch:
https://xcp-ng.com/pricing.html under "Live Patching":Enables administrators to patch hypervisors without needing to migrate, shut down or suspend VMs (no host reboots required)There has been a mistake here in the pricing page: although it's true that the live patching feature is not blocked by a license daemon as was the case in XenServer Free, we currently don't provide live patches. By the way, in the past years, many security updates were not live patchable for XenServer itself either, especially the ones related to hardware flaws in CPUs.
At least, I'd like to see if the patch requires reboot or not if possible.
We want to provide better metadata associated with updates, for XO to display. This is not ready yet, so for the time being, check the instructions for each update on the official blog. The
updatetag will list only update announcement: https://xcp-ng.org/blog/tag/update/ -
@stormi said in New patch - sudo:
Better not install security patches that require a reboot without rebooting. All you create is a discrepancy between what resides in memory and what is on disk, and in rare cases things may break, for no added security.
Isn't this only true with specific patches? I'm no expert here so really just curious. Regardless I ALWAYS plan to reboot with ANY patches coming out and think others should do the same.
@stormi said in New patch - sudo:
We want to provide better metadata associated with updates, for XO to display. This is not ready yet, so for the time being, check the instructions for each update on the official blog. The update tag will list only update announcement: https://xcp-ng.org/blog/tag/update/
This is great news, love to see it!