I'm not sure the best way to ask, I apologize for being verbose.
I'm trying to remediate a finding in Nessus, that is reporting SSL Compression DEFLATE is being detected, which triggers a vulnerability that says it could be vulnerable to the CRIME attack. I'm not sure if this is a false positive or what, but I "feel" that the culprit may be openssl.
In searching around I found the xs-openssl package on the XCP Koji thingy. Which has openssl version 1.1.1c, and in the change logs there is an entry:
* Tue Feb 19 2013 Tomas Mraz <tmraz@redhat.com> 1.0.1e-2
- disable ZLIB loading by default (due to CRIME attack)
However, from the terminal of my XCP-ng 8.2 server running openssl version returns an older version version OpenSSL 1.0.2k-fips 26 Jan 2017
In the Yum repo it shows both versions:
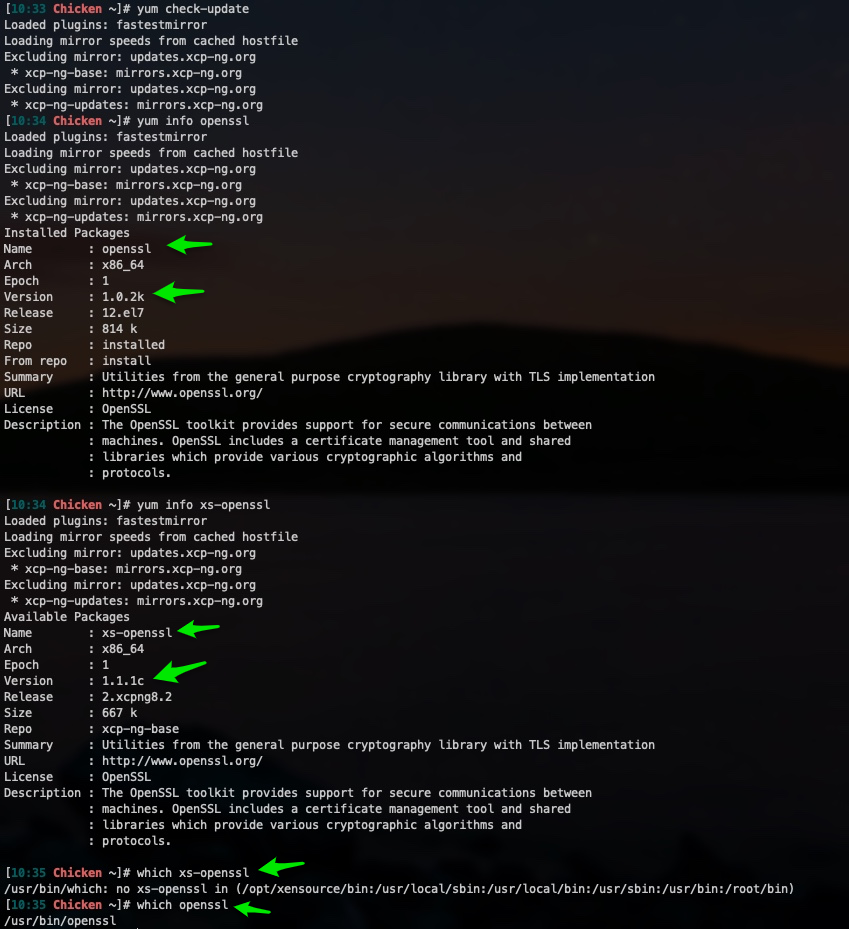
On a whim I tried to install xs-openssl but it errored out saying it conflicted with openssl.
SOOOOO, is this as intended?
Is XCP-NG using the openssl from xs-openssl or is it using the older openssl that's located in /user/bin/openssl?
Does this make any sense?
