XCP-ng Security Bulletin: XSA-278
A new bulletin, this time regarding nested VT-x usable… even when disabled! Fear not: a patch is already available in XCP-ng.
XSA-278
In short: something that should be enabled in a HVM guest can trigger Xen crashes. You can see that as a potential DDOS vector.
The whole story, quoting the XSA report itself:
When nested virtualization is disabled for the guest, it is not permitted to complete the configuration procedure. Unfortunately, when nested virtualization is intended to be disabled for the guest, an incorrect default value leads Xen to believe that the configuration procedure has already been completed.
Solution: update!
We already pushed the patches into XCP-ng repo, so it's visible -as usual- in Xen Orchestra (one click to update everything) or via a `yum update` command to run on all your hosts.
Here is what you should see in Xen Orchestra host view:
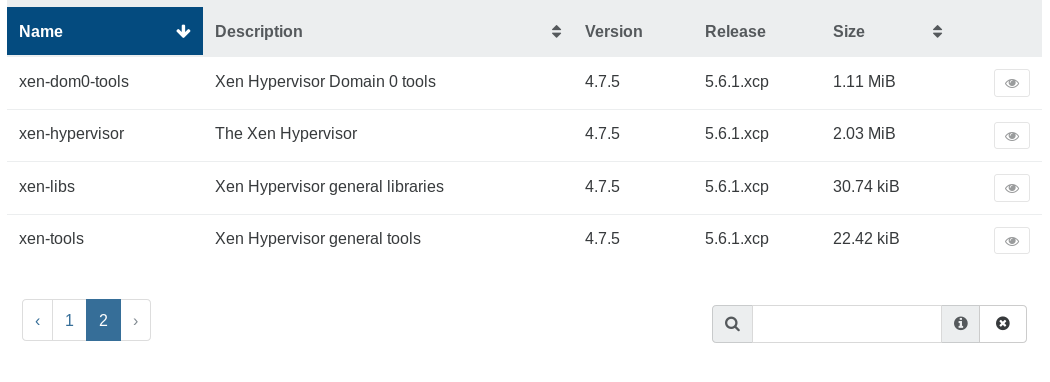
The easiest update path is to go into the pool view and click on "Install pool patches":
That's it! To take the patches into account, you'll need to reboot your hosts. It's entirely up to you to decided when to do so, just remember to keep your good habits: start with the master first.




