@olivierlambert, yes, thank you. I will open that ticket.
Best posts made by piotrlotr1
-
RE: Is there a way to assign OIDC user to local XOA group (which will have target permissions applied)?
-
RE: Is there a way to assign OIDC user to local XOA group (which will have target permissions applied)?
Is there a plan at least for the future to implement those groups from AD FS claims? Having such feature is something desirable and looks like the hardest bit is already done.
Latest posts made by piotrlotr1
-
RE: Is there a way to assign OIDC user to local XOA group (which will have target permissions applied)?
@olivierlambert, yes, thank you. I will open that ticket.
-
RE: Is there a way to assign OIDC user to local XOA group (which will have target permissions applied)?
Is there a plan at least for the future to implement those groups from AD FS claims? Having such feature is something desirable and looks like the hardest bit is already done.
-
RE: Is there a way to assign OIDC user to local XOA group (which will have target permissions applied)?
@florent In that case, every time we login for the first time via OIDC to XOA, admin will have to manually add newly created user to specific group?
There is no way to map AD FS group hidden in claim to XOA local group via some config file to automate this?
-
RE: Is there a way to assign OIDC user to local XOA group (which will have target permissions applied)?
@olivierlambert, you guys have that documentend for XCP-ng somewhere?
-
Is there a way to assign OIDC user to local XOA group (which will have target permissions applied)?
Hi,
auth-oidc plugin seems to be working fine, and we are able to login with OIDC via AD FS to our XOA.
We've also configured claim rule for target group with target user in AD FS.
Is there a documentation of how to auto assign that target user into correct XOA group (which will have target permissions applied)?
There is some info on the internet of how to do it but it's for XO not XOA I'm afraid.
-
RE: XO New Pool Master
@DustinB They were named as in column "Pool" at the very beginning - before adding them to pool.
Again, the question is why after detaching, the "Label" column shows three exactly the same names? I can rename them, but that's not the point.
I'm asking if the same "Labels" can be somehow explained...
It looks like after detaching slave host from the pool it inherits master name as a label - that doesn't look correct.
-
RE: XO New Pool Master
@DustinB No, no... look at the "Label" column.
The question is - why after detaching hosts from pool, they all have "Label" the same as pool master?
-
RE: XO New Pool Master
@olivierlambert
That worked, thank you.Next thing is that every time I hit "Detach" on any host, it jumps into "Settings -> Servers" with the same name as the host which currently is an master.
So right now I have on my "Servers" list below situation.
All three hosts have the same "Label".
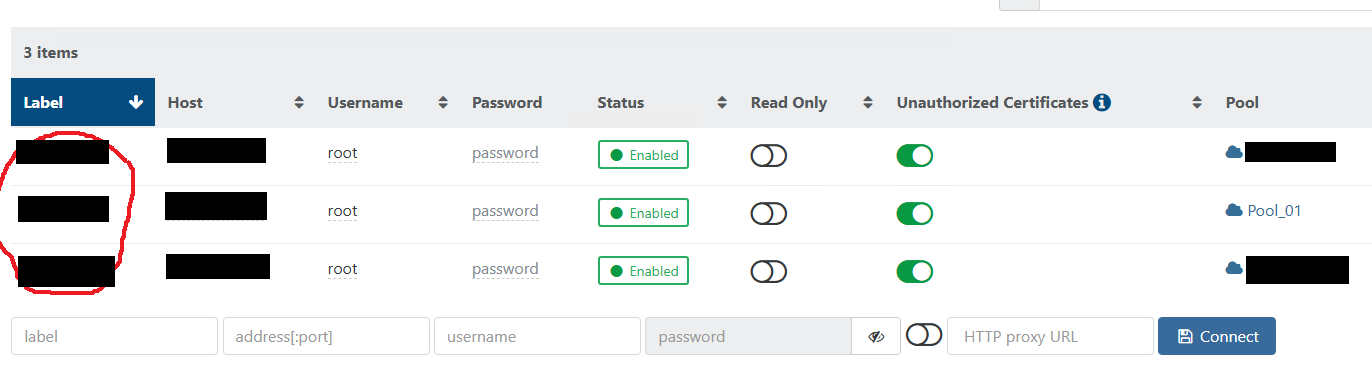
When I add them back to the pool everything goes back to normal.
I'm able to rename those without any issue but is it some kind of a bug or expected feature?
-
RE: XO New Pool Master
@olivierlambert
Well, that worked.But... after bringing back the old master (without reinstallation or anything) XOA sees it as master HOWEVER xe pool-list sees as a master different host.
-
RE: XO New Pool Master
Hello!
So it looks like after bringing master down, HA election of new one takes place however XOA is not aware of it.
Is there a way to point XOA to new master?
To check which host is the new master I've logged via SSH to one of the slaves and did below.
[05:40 phx01xcp03 ~]# xe pool-list uuid ( RO) : 03e8733b-fbd0-61c9-3850-353bfd9e3149 name-label ( RW): Pool_01 name-description ( RW): master ( RO): a65dcfcb-8a60-4aa8-a467-2351140f80d4 default-SR ( RW): <not in database>Which shows UUID of newly elected master.
[05:52 phx01xcp03 ~]# xe host-list uuid=a65dcfcb-8a60-4aa8-a467-2351140f80d4 uuid ( RO) : a65dcfcb-8a60-4aa8-a467-2351140f80d4 name-label ( RW): hidden_label name-description ( RW): Default installNot sure why default-SR has "<not in database>" status.