OAuth and OKTA
-
I am playing with the XO installation using the open source and the OAuth. While trying to get the OAuth working I keep running into an issue where the redirect URI fails.
Following the directions in the https://login.my domain.com/ should work. but instead, I get the following error. "Your request resulted in an error. The 'redirect_uri' parameter must be a Login redirect URI in the client app settings: " Does anyone have any suggestions on what it may look for in this URI?
-
Solved. After a bit more playing around I finally figured it out.
In the Configuration for XOA set the following in the "AutoDiscovery URL" https://{Yourdomainname}.okta.com/.well-known/openid-configuration. Do not fill in any of the Advanced fields. They will work just fine.
Then in OKTA for the 'Sign in' redirect URLs put in the following. https://{Your XO servername}/signin/oidc/callback if you access the server through multiple URLs you may need to add additional lines.
Make sure you have the PKCE checkbox turned off or you will get a 500 server error on the client side. The OIDC plugin does not like to use PKCE.
If you choose to have the option of "Login Initiated by" set to either OKTA or App then you will need to set the "Initiate login URI" to be the same as your 'Sign in' redirect. This way you can have your XOA control panel in your list of available SAAS apps in your OKTA browser plugin for authorized users.
Leave off the wildcard checkbox since it just makes you less safe.
This should help anyone else who is not an OIDC expert figure out how to make XOA behave with your OKTA installation, hopefully, this will help out the next person who runs in this challenge.
-
@erlicthemad said in OAuth and OKTA:
I am playing with the XO installation using the open source and the OAuth. While trying to get the OAuth working I keep running into an issue where the redirect URI fails.
Following the directions in the https://login.my domain.com/ should work. but instead, I get the following error. "Your request resulted in an error. The 'redirect_uri' parameter must be a Login redirect URI in the client app settings: " Does anyone have any suggestions on what it may look for in this URI?
So I don't use Okta, but do have SSO setup. What I had to use for my call back was what would generally be publicly routable, to get around this you can add the DNS name to your DNS server as an A record with the specific IP address.
IE: XO.domain.com for the Redirect URI
It doesn't actually need to publicly routable though
-
@DustinB I do have that. Internally its called https://xoa-os.lcco.co.lucas.oh.us which redirects to https://xoa-os.lcco.co.lucas.oh.us/signin .
Your suggestion was one of the first things I tried. just put https://xoa-os.lcco.co.lucas.oh.us/ then https://xoa-os.lcco.co.lucas.oh.us/* at both my redirect URLs usually that's all I need to have it work.
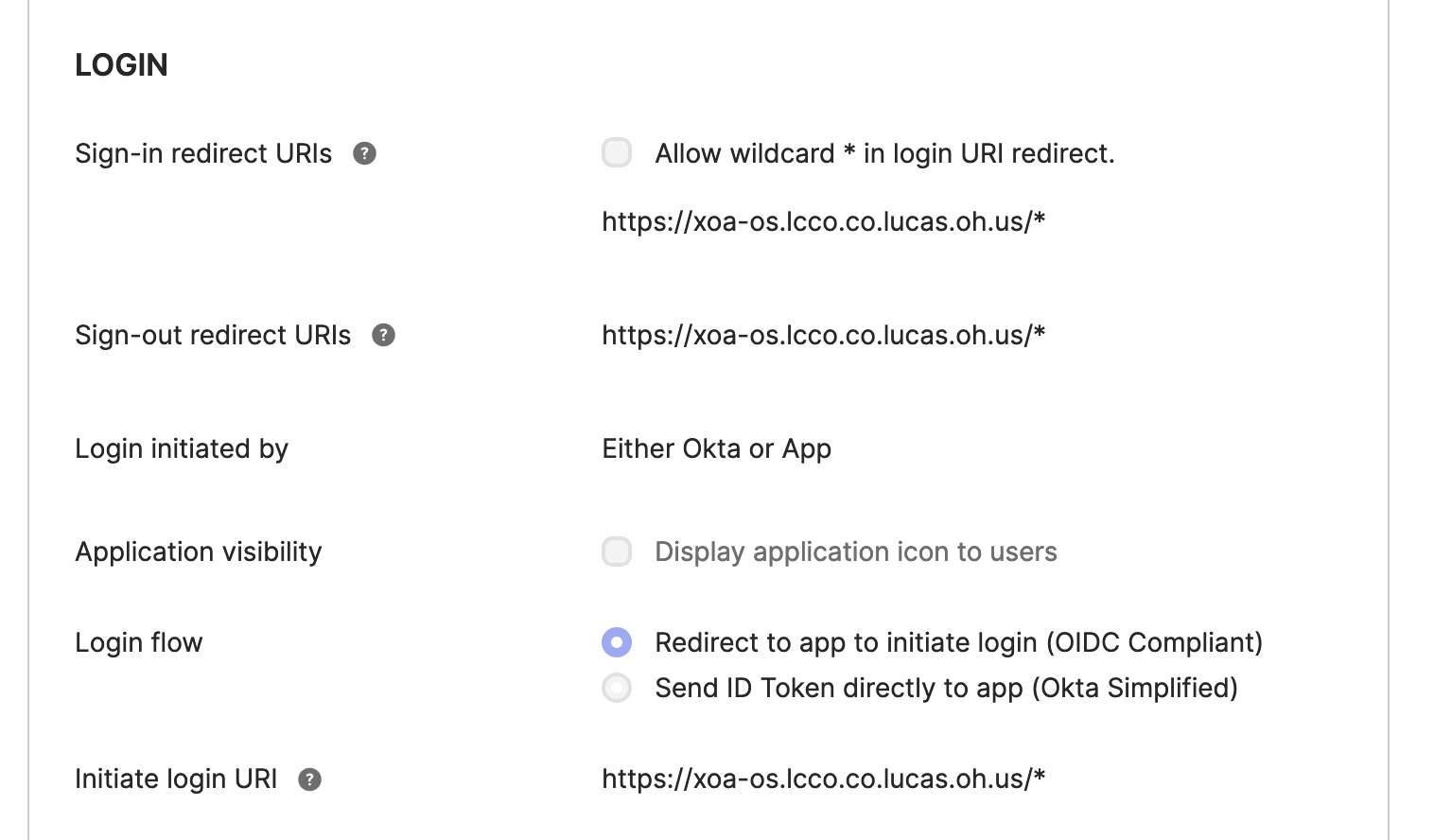
none of these URIs are externally visible or routable outside. But to the browser, it works correctly. Or are you suggesting that I have to have the DNS name exposed externally? That would require that I create an A record in the public DNS, which I would rather not do.
-
This post is deleted! -
Solved. After a bit more playing around I finally figured it out.
In the Configuration for XOA set the following in the "AutoDiscovery URL" https://{Yourdomainname}.okta.com/.well-known/openid-configuration. Do not fill in any of the Advanced fields. They will work just fine.
Then in OKTA for the 'Sign in' redirect URLs put in the following. https://{Your XO servername}/signin/oidc/callback if you access the server through multiple URLs you may need to add additional lines.
Make sure you have the PKCE checkbox turned off or you will get a 500 server error on the client side. The OIDC plugin does not like to use PKCE.
If you choose to have the option of "Login Initiated by" set to either OKTA or App then you will need to set the "Initiate login URI" to be the same as your 'Sign in' redirect. This way you can have your XOA control panel in your list of available SAAS apps in your OKTA browser plugin for authorized users.
Leave off the wildcard checkbox since it just makes you less safe.
This should help anyone else who is not an OIDC expert figure out how to make XOA behave with your OKTA installation, hopefully, this will help out the next person who runs in this challenge.
-
 O olivierlambert marked this topic as a question on
O olivierlambert marked this topic as a question on
-
 O olivierlambert has marked this topic as solved on
O olivierlambert has marked this topic as solved on
-
Thanks for your feedback @erlicthemad !