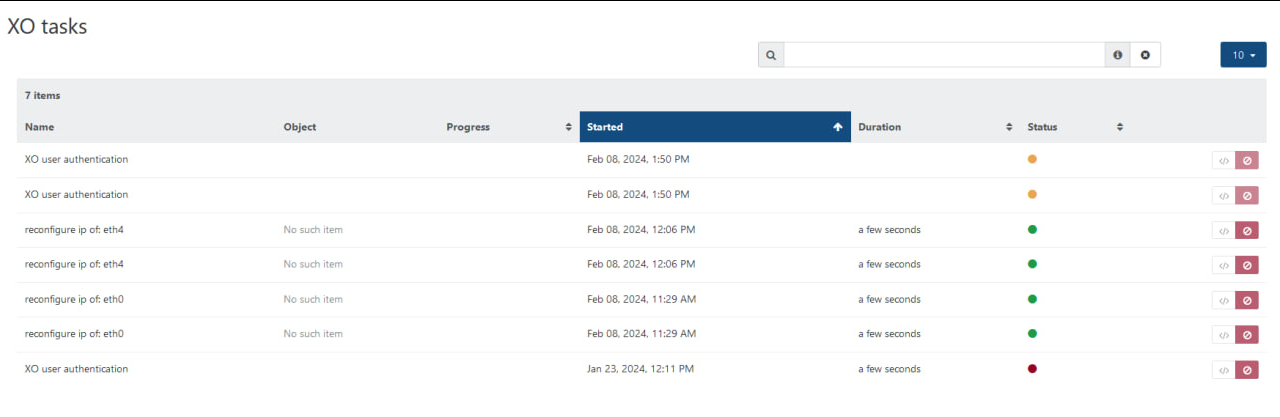
NBD setup - No such item
-
@florent as i say, XO only one interface it's same host interface where NBD is enabled.
-
@Tristis-Oris And you don't have message like
can't connect to nbd serverin the system log / Xo-server output ? -
@florent never seen such errors. At which step it should happens?
-
@Tristis-Oris when launching a backup, between the snapshot and the beginning of the the transfer. It should try to connect to the host(s) NBD server
-
@florent also , is there a firewall/network filtering between XO and the host ? the conneciton to the NBD server go through the port 10809
-
@florent is NBD server running at dom0?
for clear test: disabled nbd, removed all XO logs. Enabled NBD on host, changed XO interface to this one, run backup task with NBD > no one error at logs.
-
@Tristis-Oris yes the NBD server run in the dom0, one per host
-
@florent hm. Telnet to 10809 is refused even from dom0, to both backup interface and management.
We have no any additional firewalls at network. Host's iptable looks fine.What a name of service, to check if it running?
-
also add
filter = 'xo:backups:DeltaBackupWriter'to config.toml. Anyway no one error during backup. -
@Tristis-Oris I think it is built in in the xapi .
ss -tulpnon my host :
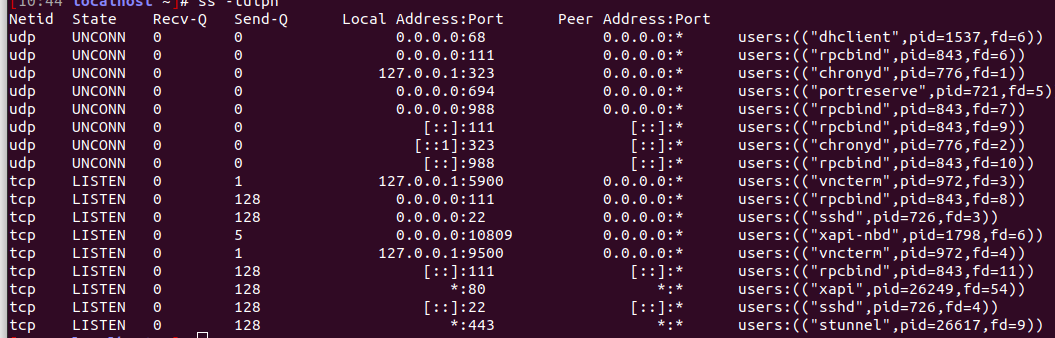
there is a xapi-nbd service
-
@florent looks fine.
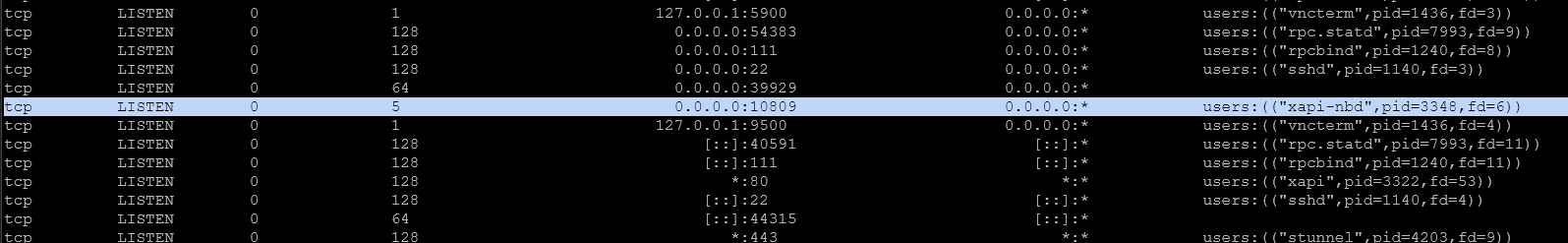
also i add extra iptables rules, nothing changed.
iptables -A INPUT -p tcp --dport 10809 -m comment --comment "NBD" -j ACCEPT iptables -A OUTPUT -p tcp --dport 10809 -m comment --comment "NBD" -j ACCEPT -
@Tristis-Oris my iptable are
-P INPUT ACCEPT -P FORWARD ACCEPT -P OUTPUT ACCEPT -N RH-Firewall-1-INPUT -N xapi_nbd_input_chain -N xapi_nbd_output_chain -A INPUT -p tcp -m tcp --dport 10809 -j xapi_nbd_input_chain -A INPUT -p gre -j ACCEPT -A INPUT -j RH-Firewall-1-INPUT -A FORWARD -j RH-Firewall-1-INPUT -A OUTPUT -p tcp -m tcp --sport 10809 -j xapi_nbd_output_chain -A RH-Firewall-1-INPUT -i lo -j ACCEPT -A RH-Firewall-1-INPUT -p icmp -m icmp --icmp-type any -j ACCEPT -A RH-Firewall-1-INPUT -i xenapi -p udp -m udp --dport 67 -j ACCEPT -A RH-Firewall-1-INPUT -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT -A RH-Firewall-1-INPUT -p udp -m conntrack --ctstate NEW -m udp --dport 694 -j ACCEPT -A RH-Firewall-1-INPUT -p tcp -m conntrack --ctstate NEW -m tcp --dport 22 -j ACCEPT -A RH-Firewall-1-INPUT -p tcp -m conntrack --ctstate NEW -m tcp --dport 80 -j ACCEPT -A RH-Firewall-1-INPUT -p tcp -m conntrack --ctstate NEW -m tcp --dport 443 -j ACCEPT -A RH-Firewall-1-INPUT -p tcp -m tcp --dport 21064 -j ACCEPT -A RH-Firewall-1-INPUT -p udp -m multiport --dports 5404,5405 -j ACCEPT -A RH-Firewall-1-INPUT -j REJECT --reject-with icmp-host-prohibited -A xapi_nbd_input_chain -i xenbr0 -m conntrack --ctstate NEW,ESTABLISHED -j ACCEPT -A xapi_nbd_input_chain -j REJECT --reject-with icmp-port-unreachable -A xapi_nbd_output_chain -o xenbr0 -j RETURN -A xapi_nbd_output_chain -j REJECT --reject-with icmp-port-unreachablethere is already a line for nbd
-
@florent everything is default except NBD rule. looks similar.
Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 16 960 xapi_nbd_input_chain tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:10809 0 0 ACCEPT 47 -- * * 0.0.0.0/0 0.0.0.0/0 9872M 155T RH-Firewall-1-INPUT all -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:10809 /* NBD */ 0 0 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:10809 /* NBD */ Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 RH-Firewall-1-INPUT all -- * * 0.0.0.0/0 0.0.0.0/0 Chain OUTPUT (policy ACCEPT 22M packets, 34G bytes) pkts bytes target prot opt in out source destination 0 0 xapi_nbd_output_chain tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp spt:10809 4 240 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:10809 /* NBD */ 0 0 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:10809 /* NBD */ Chain RH-Firewall-1-INPUT (2 references) pkts bytes target prot opt in out source destination 341M 9622G ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 29 5104 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 255 0 0 ACCEPT udp -- xenapi * 0.0.0.0/0 0.0.0.0/0 udp dpt:67 9530M 146T ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 0 0 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 ctstate NEW udp dpt:694 1 52 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 ctstate NEW tcp dpt:22 65232 3914K ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 ctstate NEW tcp dpt:80 488K 29M ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 ctstate NEW tcp dpt:443 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:21064 0 0 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 multiport dports 5404,5405 588K 4800M REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain xapi_nbd_input_chain (1 references) pkts bytes target prot opt in out source destination 0 0 ACCEPT all -- xenbr0 * 0.0.0.0/0 0.0.0.0/0 ctstate NEW,ESTABLISHED 16 960 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-port-unreachable Chain xapi_nbd_output_chain (1 references) pkts bytes target prot opt in out source destination 0 0 RETURN all -- * xenbr0 0.0.0.0/0 0.0.0.0/0 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-port-unreachable -
after telnet request to 10809, rejected packages increased.
Chain xapi_nbd_input_chain (1 references) pkts bytes target prot opt in out source destination 0 0 ACCEPT all -- xenbr0 * 0.0.0.0/0 0.0.0.0/0 ctstate NEW,ESTABLISHED 17 1020 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-port-unreachable -
if i have no errors during backup, it means XO didn't try to use NBD?
but at begining of each NBD backup i got +1 to iptables rejected list.
-
@Tristis-Oris said in NBD setup - No such item:
but at begining of each NBD backup i got +1 to iptables rejected list.
I think there is something with the network configuration, but I am far out of my element here .
-
@florent is it any requirements for network\switch etc. Any layers outside of Xen.
-
@Tristis-Oris it hae to let the encrypted traffic flow through the 10809 port. XO will connect directly to the hosts through NBD, not only to the master
-
@florent sounds pretty simple. Nothing at my network should block that traffic.
Anyway, if i got rejected packets at iptables - backup task try to connect NBD server. Then it can't do something, so i should get an error at XO, but it not happens.
-
No such itemtask happens when host interface at statusnonewithout IP.