Citrix Hypervisor 8.1 released
-
I'm not happy to see DMC dropping, but even more removal of "VSS and quiesced snapshots" is sad.
It's probably one more step from general Hypervisor solution to VDI, as it's not really important there, but if you have DB servers etc... -
-
@olivierlambert the idea of iptables for the VM, Ansible etc. were just other options I looked into as alternatives because DVSC was not my first choice option due to its limitations of only supporting IE and the "heavy" DVSC appliance
The specific feature that I wanted to use is the "Access Control policies" to achieve something similar to AWS security groups. https://docs.citrix.com/en-us/citrix-hypervisor/vswitch-controller/virtual-network-visibility.html#set-up-access-control-policies
-
@GHW @olivierlambert The Access Control lists in the DVSC instance was easily one of its most powerful and useful features. It essentially turned the DVS into an actual port-level security capable virtual switch. If it had full-featured routing, it would have been a very nifty solution to layer 3 in the virtual network space without having to run an entirely different appliance to achieve that capability. Perhaps that is something that the SDN could do at some point? (become a layer 3 capable switch with security access control)
-
Sadly I have no DVSC knowledge myself, so it would be great if you are able to explain in a kind of simple "high level specification" (eh "doing this in the UI with a screenshot, it does that") in a Github issue for SDN plugin, we might implement it on our side

-
So does the removal of the DMC mean that we wont be able to over-commit memory anymore?
Regards,
Marty -
@olivierlambert said in Citrix Hypervisor 8.1 released:
Sadly I have no DVSC knowledge myself, so it would be great if you are able to explain in a kind of simple "high level specification" (eh "doing this in the UI with a screenshot, it does that") in a Github issue for SDN plugin, we might implement it on our side

A bit of good news is that the DVSC works out of the box with XCP-ng 8.0. Though I have not tested it in conjunction with the SDN plug-in.
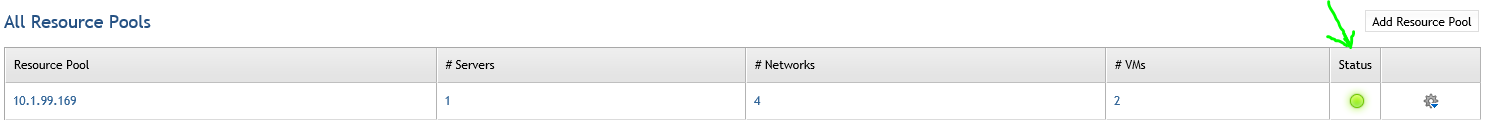
After importing the DVSC and adding it to the resource pool:
.1) Select the VM you want to apply security ACLs to
.2) Select "Access Control" and here you can create a network ACL policy to control traffic to and from the VM (by default there are no restrictions)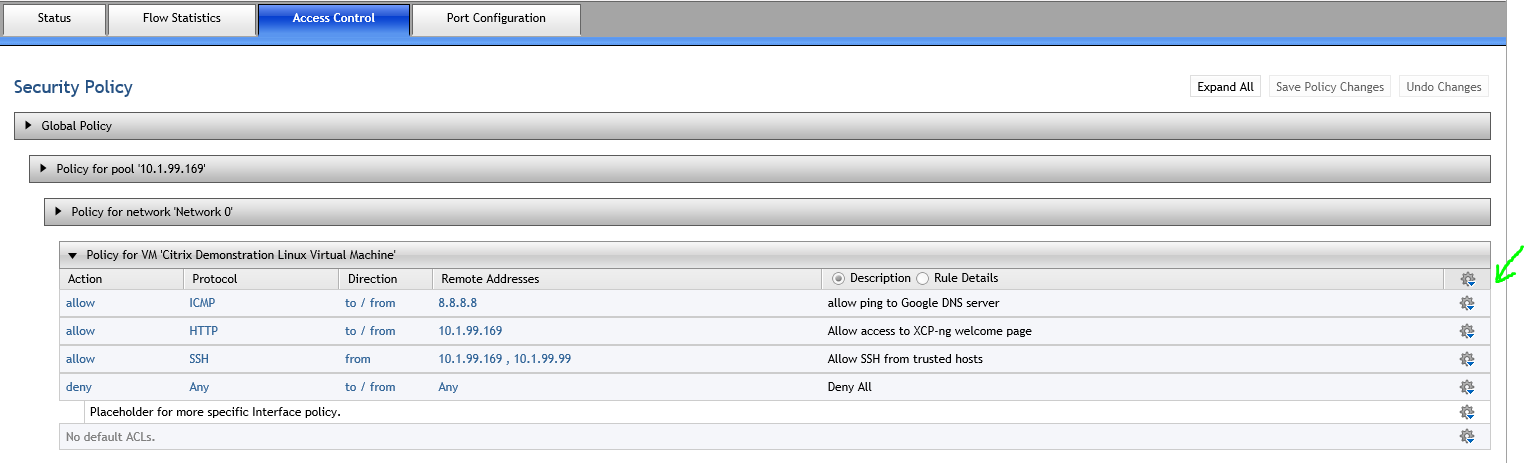
.3) Apply your desired network security policy to the VM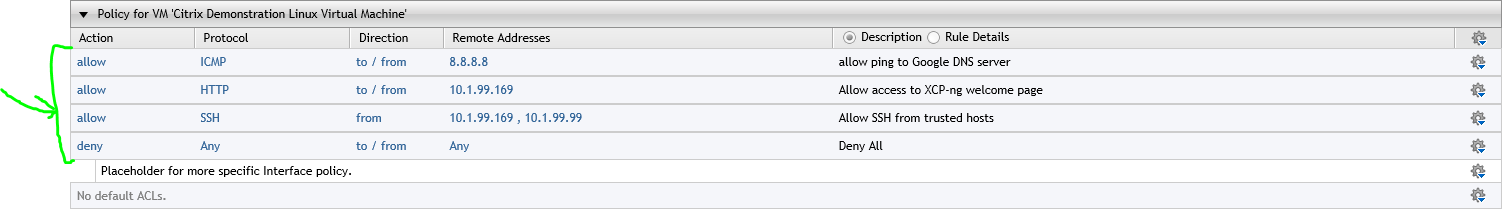
Results
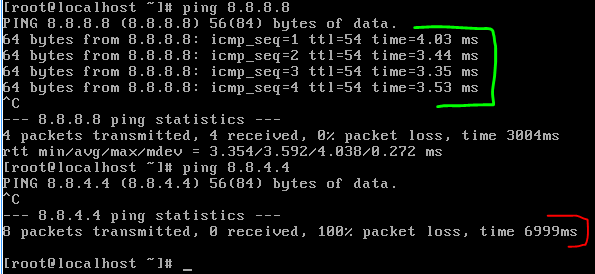
Allows ping to 8.8.8.8 but blocks ping to 8.8.4.4 since it is not allowed in ACL policy
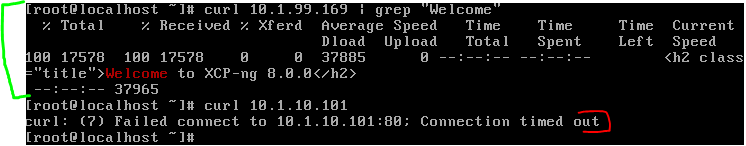
Allows access to HTTP web server as defined in the the VM network ACL policy and blocks access to the other
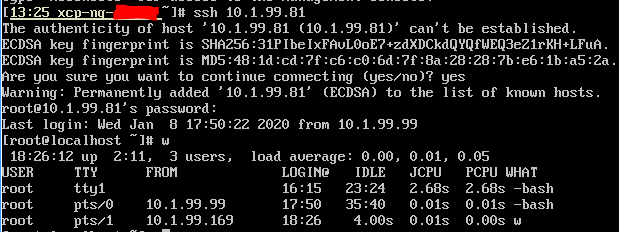
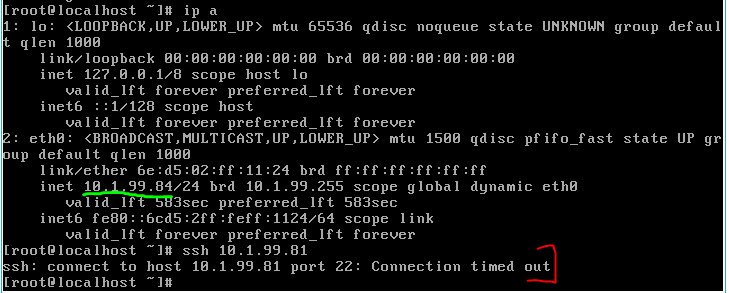
Restricts SSH access to trusted hosts
-
Thanks I'm pinging @BenjiReis who built the SDN plugin

-
@olivierlambert thanks

-
@GHW this is in our internal roadmap. So before doing any promises, we'll see first if we can do a working PoC. Depending on priorities, we could target a firm answer (will it be released one day) in Q1, and if yes to the previous question, might be Q2.
-
@olivierlambert Awesome and thank you for the follow-up.
Hello! It looks like you're interested in this conversation, but you don't have an account yet.
Getting fed up of having to scroll through the same posts each visit? When you register for an account, you'll always come back to exactly where you were before, and choose to be notified of new replies (either via email, or push notification). You'll also be able to save bookmarks and upvote posts to show your appreciation to other community members.
With your input, this post could be even better 💗
Register Login