OpenSSL vs XS-OpenSSL?
-
I'm not sure the best way to ask, I apologize for being verbose.
I'm trying to remediate a finding in Nessus, that is reporting SSL Compression DEFLATE is being detected, which triggers a vulnerability that says it could be vulnerable to the CRIME attack. I'm not sure if this is a false positive or what, but I "feel" that the culprit may be openssl.
In searching around I found the xs-openssl package on the XCP Koji thingy. Which has openssl version 1.1.1c, and in the change logs there is an entry:
* Tue Feb 19 2013 Tomas Mraz <tmraz@redhat.com> 1.0.1e-2 - disable ZLIB loading by default (due to CRIME attack)However, from the terminal of my XCP-ng 8.2 server running
openssl versionreturns an older version version OpenSSL 1.0.2k-fips 26 Jan 2017In the Yum repo it shows both versions:
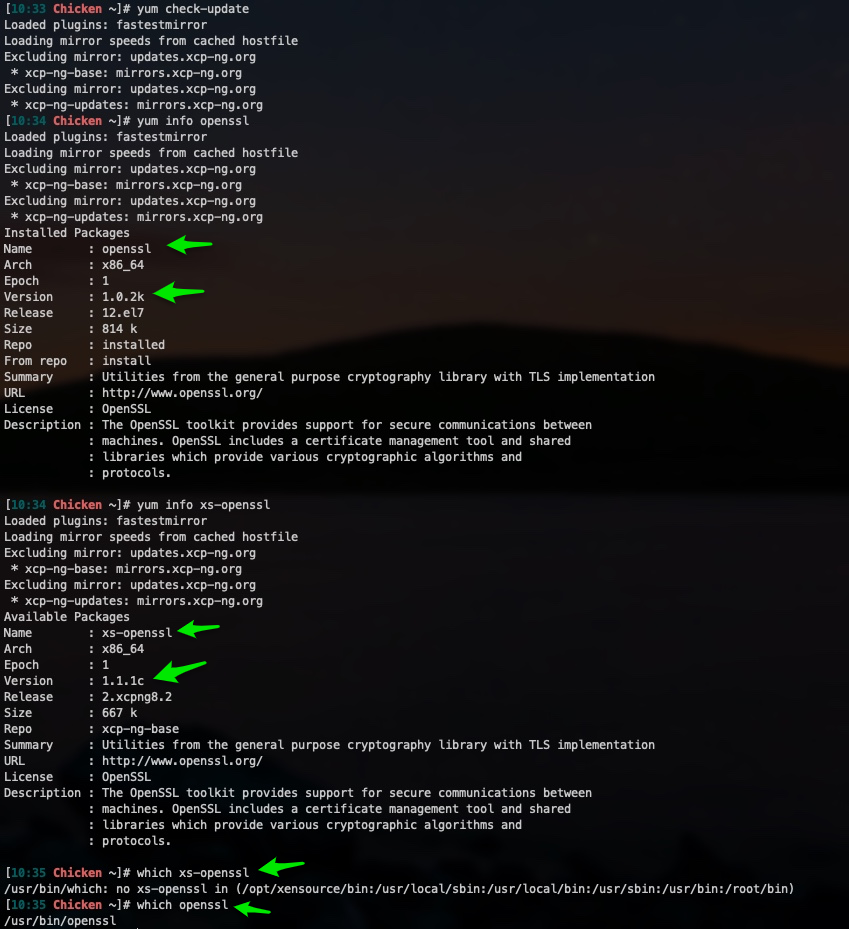
On a whim I tried to install xs-openssl but it errored out saying it conflicted with openssl.
SOOOOO, is this as intended?
Is XCP-NG using the openssl from xs-openssl or is it using the older openssl that's located in /user/bin/openssl?Does this make any sense?
-
-
Yes, the situation is not simple.
The base openssl version is from the CentOS openssl RPM, running in version 1.0.2k. Any piece of software on the server that needs openssl will use this except:
blktapandstunnel(which is used to encapsulate traffic between hosts). Those two are built against xs-openssl and thus link against xs-openssl-libs.On Citrix Hypervisor, there exists a third version of openssl, because they use
citrix-crypto-module, a closed-source openssl with FIPS support, for the certification of their product, instead of xs-openssl. -
This post is deleted! -
@stormi Thank you for your response!
BTW, I fell down a rabbit hole, the OpenSSL FIPS Provider 3.0 was submitted for testing Oct of 2020. It's currently on the Implementation Under Test List. It would be very cool if XCP-ng were to be able to leverage that in the future. As I'm in the process of getting XCP-ng approved for a branch of the dep of def. If I can get that through, I'd like to get XOA approved as well.
-
Hello! It looks like you're interested in this conversation, but you don't have an account yet.
Getting fed up of having to scroll through the same posts each visit? When you register for an account, you'll always come back to exactly where you were before, and choose to be notified of new replies (either via email, or push notification). You'll also be able to save bookmarks and upvote posts to show your appreciation to other community members.
With your input, this post could be even better 💗
Register Login