How to protect a VM and Disks from accidental exclusion
-
Hello everyone!
We want to protect some VMs and associated disks from being deleted (acidental or proposal). The command below protects the VM from being deleted but not the associated disks:
xe vm-param-set uuid=<UUID_OF_THE_VM> blocked-operations:destroy=true
What parameter is missing to be included?
Thanks!!
-
@dfrizon said in How to protect a VM and Disks from accidental exclusion:
Hello everyone!
We want to protect some VMs and associated disks from being deleted (acidental or proposal). The command below protects the VM from being deleted but not the associated disks:
xe vm-param-set uuid=<UUID_OF_THE_VM> blocked-operations:destroy=true
What parameter is missing to be included?
Thanks!!
Within XO this is very straight-forward. Under the VM's advanced details tab
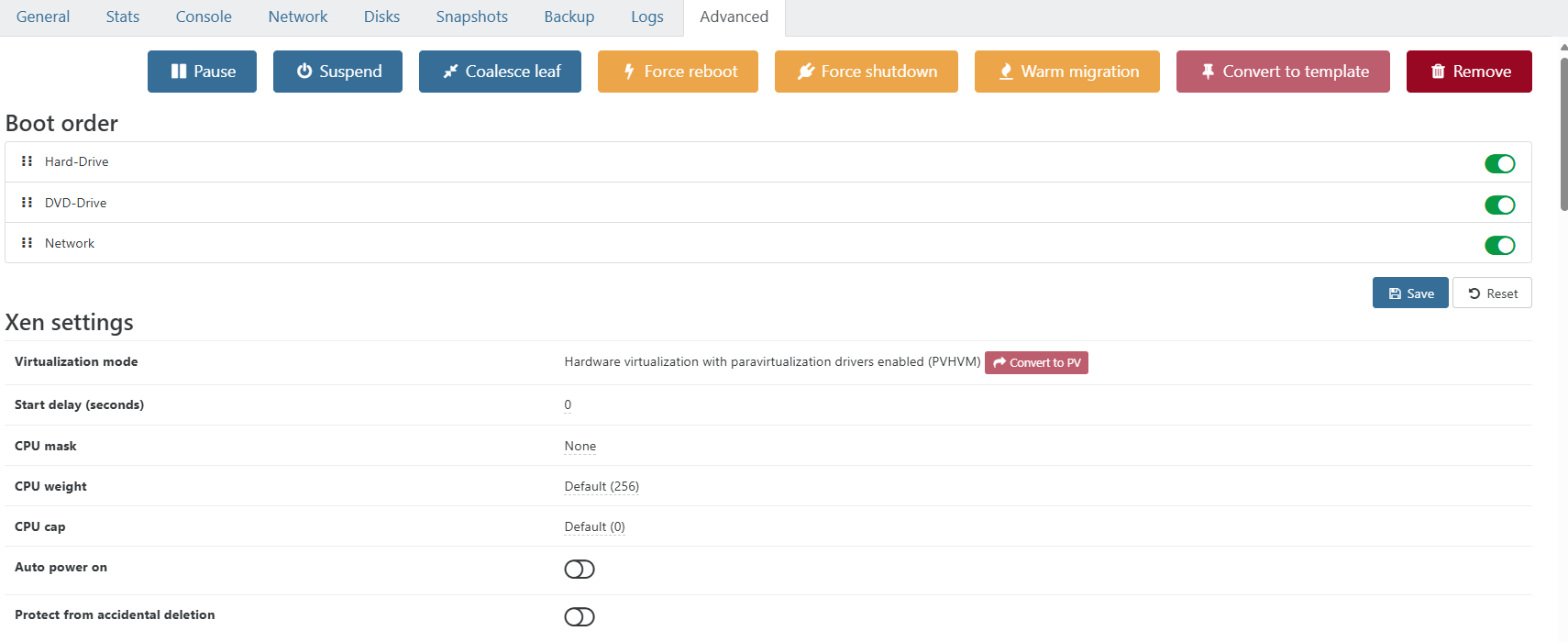
-
@DustinB Thanks for the quick answer, but the problem is "how to protect the DISKS from accidental exclusion". The VM protection is ok, but if you go to the disks tab you can delete de disk, that is worst that delete a VM...
-
You have a confirmation modal when you try to remove a drive. Can you describe more your use case, functionally speaking?
-
While the system prevents you from deleting as VM's disk while the vm is running. There is nothing to stop you from deleteing a disk to a vm that is powered off.
The check box under advance for the vm just protects the VM itself but not the disk seperatatly.
I guess they have some staff that like to clean up things that should be left alone... thats my take.
-
@olivierlambert The idea is to block the VM and exclusion disks even by root itself, and make it possible only via command line in the console. That's why I started the post by mentioning the command...
We dream of the day when MFA authentication will be required to delete a VM... -
@dfrizon said in How to protect a VM and Disks from accidental exclusion:
@olivierlambert The idea is to block the VM and exclusion disks even by root itself, and make it possible only via command line in the console. That's why I started the post by mentioning the command...
We dream of the day when MFA authentication will be required to delete a VM...How would you prevent the root account from taking action..... that is the absolute opposite permission set of root, as if there is an account with even more permissions than root.
You can use permission sets and move your team who are deleting powered off VM's that are protected from accidental deletion into a group that doesn't have the permission to delete VMs, at the same time, remove their permissions from deleting items from your SR.
I think that would solve your problem, and doesn't cause any logical permission issues like above.
Hello! It looks like you're interested in this conversation, but you don't have an account yet.
Getting fed up of having to scroll through the same posts each visit? When you register for an account, you'll always come back to exactly where you were before, and choose to be notified of new replies (either via email, or push notification). You'll also be able to save bookmarks and upvote posts to show your appreciation to other community members.
With your input, this post could be even better 💗
Register Login