8.3 USB Passthrough - Win Server 2019 BSOD
-
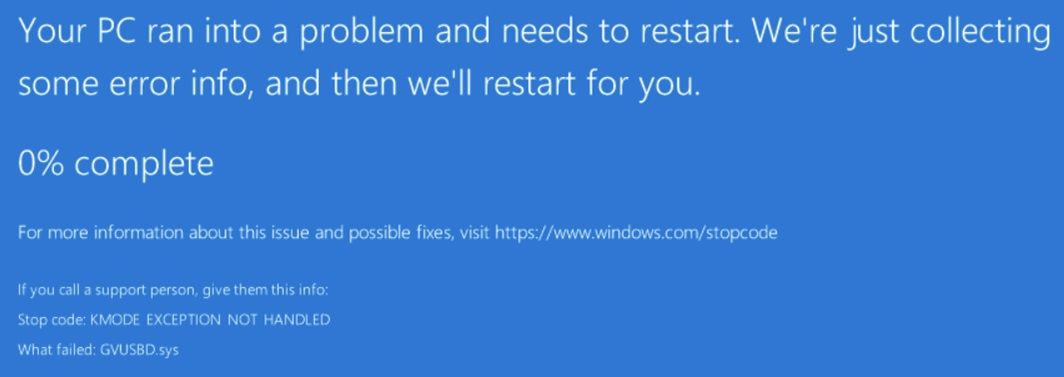
We've been running 8.2 for a while now and one of our VMs has a USB passthrough attached (GeoVision Licensing Dongle). After upgrading to to 8.3 over the weekend our issue began. The VM will boot and operate without issue, until I run GeoVision's ASManager, which accesses the USB drive for its licensing. At which time the system BSODs with a
Stop Code: KMODE EXCEPTION NOT HANDLED
What failed: GVUSBD.sysAny suggestions on how to fix this? Or other logs I can provide to troubleshoot?
Andrew
 -
I've tried removing the VUSB drive and recreating it, still the same result.
@olivierlambert no ideas on this?
-
Hi,
No, but maybe @dinhngtu does.
-
It looks like the GeoVision dongle's driver is failing somehow. Could you open the crash dump with Windbg, run the command
!analyze -vand post its output? -
@dinhngtu Sorry, I failed to mention this is a Windows Server 2019 VM, it appears that Windbg is a Windows 10/11 application. I've googled installing on Server 2019, but haven't had any luck getting it installed.
-
@andsmith said in 8.3 USB Passthrough - Win Server 2019 BSOD:
@dinhngtu Sorry, I failed to mention this is a Windows Server 2019 VM, it appears that Windbg is a Windows 10/11 application. I've googled installing on Server 2019, but haven't had any luck getting it installed.
Update the AppX Package Deployment software via Microsoft Store or its equivalent in Windows Server 2019. Then once winget is updated (or installed) run the following command:
winget install Microsoft.WinDbg
@olivierlambert If this works for andsmith then it may be worth documenting this, for future users of Windows Server 2019, 2022 and possibly if required the upcoming Windows Server 2025.
-
Agreed

-
@olivierlambert said in 8.3 USB Passthrough - Win Server 2019 BSOD:
Agreed

Oh also this includes Windows Server 2016 and also if not present then Windows 10 and 11.
Anyway just thought I would help out the user with the method of installing WinDbg on their server VM.
While waiting to be pinged back later by a poster with the Epyc network bug, worth checking out the latest responses to that bug on the forums.
-
@john-c said in 8.3 USB Passthrough - Win Server 2019 BSOD:
winget install Microsoft.WinDbg
Following information from this website
I've run the following commands in PowerShell:
Install-Script -Name winget-install winget-installThese ran without issue, however when I ran the command:
winget install Microsoft.WinDbgThe installer starts, but fails with the error:
InstallFlowReturnCodeBlockedByPolicy InstallerFailedWithCode -
@andsmith said in 8.3 USB Passthrough - Win Server 2019 BSOD:
@john-c said in 8.3 USB Passthrough - Win Server 2019 BSOD:
winget install Microsoft.WinDbg
Following information from this here
I've run the following commands in PowerShell:
Install-Script -Name winget-install winget-installThese ran without issue, however when I ran the command:
winget install Microsoft.WinDbgThe installer starts, but fails with the error:
InstallFlowReturnCodeBlockedByPolicy InstallerFailedWithCodeThat's a reference to GroupPolicy settings applied which affect the software installation of Appx Packages, as well as possibly other relevant policies. As well as any Conditional Access policies applied which affected the installation, these policies can also come from services like Microsoft Entra etc.
-
@andsmith Another method if that doesn't work for you:
- Enable sideloading apps in Developer settings
- Get the Appinstaller file from https://learn.microsoft.com/en-us/windows-hardware/drivers/debugger/ (Install WinDbg directly)
- Open it with Notepad and download the .msixbundle file from the MainBundle URI
- Install the .msixbundle with Add-Appxpackage
-
@dinhngtu said in 8.3 USB Passthrough - Win Server 2019 BSOD:
@andsmith Another method if that doesn't work for you:
- Enable sideloading apps in Developer settings
- Get the Appinstaller file from https://learn.microsoft.com/en-us/windows-hardware/drivers/debugger/ (Install WinDbg directly)
- Open it with Notepad and download the .msixbundle file from the MainBundle URI
- Install the .msixbundle with Add-Appxpackage
Following these instruction I was able to get Windbg installed and running. Having never done this before, I believe what you are after is below, please let me know.
For analysis of this file, run !analyze -v nt!KeBugCheckEx: fffff802`6e0586e0 48894c2408 mov qword ptr [rsp+8],rcx ss:0018:ffff920e`9a9ac910=000000000000001e 1: kd> !analyze -v ******************************************************************************* * * * Bugcheck Analysis * * * ******************************************************************************* KMODE_EXCEPTION_NOT_HANDLED (1e) This is a very common BugCheck. Usually the exception address pinpoints the driver/function that caused the problem. Always note this address as well as the link date of the driver/image that contains this address. Arguments: Arg1: ffffffffc0000096, The exception code that was not handled Arg2: fffff804db200407, The address that the exception occurred at Arg3: 0000000000000000, Parameter 0 of the exception Arg4: 0000000000000000, Parameter 1 of the exception Debugging Details: ------------------ ************************************************************************* *** *** *** *** *** Either you specified an unqualified symbol, or your debugger *** *** doesn't have full symbol information. Unqualified symbol *** *** resolution is turned off by default. Please either specify a *** *** fully qualified symbol module!symbolname, or enable resolution *** *** of unqualified symbols by typing ".symopt- 100". Note that *** *** enabling unqualified symbol resolution with network symbol *** *** server shares in the symbol path may cause the debugger to *** *** appear to hang for long periods of time when an incorrect *** *** symbol name is typed or the network symbol server is down. *** *** *** *** For some commands to work properly, your symbol path *** *** must point to .pdb files that have full type information. *** *** *** *** Certain .pdb files (such as the public OS symbols) do not *** *** contain the required information. Contact the group that *** *** provided you with these symbols if you need this command to *** *** work. *** *** *** *** Type referenced: ExceptionRecord *** *** *** ************************************************************************* ************************************************************************* *** *** *** *** *** Either you specified an unqualified symbol, or your debugger *** *** doesn't have full symbol information. Unqualified symbol *** *** resolution is turned off by default. Please either specify a *** *** fully qualified symbol module!symbolname, or enable resolution *** *** of unqualified symbols by typing ".symopt- 100". Note that *** *** enabling unqualified symbol resolution with network symbol *** *** server shares in the symbol path may cause the debugger to *** *** appear to hang for long periods of time when an incorrect *** *** symbol name is typed or the network symbol server is down. *** *** *** *** For some commands to work properly, your symbol path *** *** must point to .pdb files that have full type information. *** *** *** *** Certain .pdb files (such as the public OS symbols) do not *** *** contain the required information. Contact the group that *** *** provided you with these symbols if you need this command to *** *** work. *** *** *** *** Type referenced: ContextRecord *** *** *** ************************************************************************* KEY_VALUES_STRING: 1 Key : Analysis.CPU.mSec Value: 3562 Key : Analysis.Elapsed.mSec Value: 3659 Key : Analysis.IO.Other.Mb Value: 0 Key : Analysis.IO.Read.Mb Value: 0 Key : Analysis.IO.Write.Mb Value: 23 Key : Analysis.Init.CPU.mSec Value: 1608 Key : Analysis.Init.Elapsed.mSec Value: 187592 Key : Analysis.Memory.CommitPeak.Mb Value: 90 Key : Bugcheck.Code.KiBugCheckData Value: 0x1e Key : Bugcheck.Code.LegacyAPI Value: 0x1e Key : Bugcheck.Code.TargetModel Value: 0x1e Key : Failure.Bucket Value: 0x1E_C0000096_GVUSBD!unknown_function Key : Failure.Hash Value: {e33840ed-d273-c482-6ab3-fda3f8b1b7cf} Key : Hypervisor.Enlightenments.Value Value: 112 Key : Hypervisor.Enlightenments.ValueHex Value: 70 Key : Hypervisor.Flags.AnyHypervisorPresent Value: 1 Key : Hypervisor.Flags.ApicEnlightened Value: 1 Key : Hypervisor.Flags.AsyncMemoryHint Value: 0 Key : Hypervisor.Flags.CpuManager Value: 0 Key : Hypervisor.Flags.DeprecateAutoEoi Value: 0 Key : Hypervisor.Flags.DynamicCpuDisabled Value: 0 Key : Hypervisor.Flags.Epf Value: 0 Key : Hypervisor.Flags.ExtendedProcessorMasks Value: 0 Key : Hypervisor.Flags.HardwareMbecAvailable Value: 0 Key : Hypervisor.Flags.MaxBankNumber Value: 0 Key : Hypervisor.Flags.MemoryZeroingControl Value: 0 Key : Hypervisor.Flags.NoExtendedRangeFlush Value: 1 Key : Hypervisor.Flags.NoNonArchCoreSharing Value: 0 Key : Hypervisor.Flags.Phase0InitDone Value: 1 Key : Hypervisor.Flags.PowerSchedulerQos Value: 0 Key : Hypervisor.Flags.RootScheduler Value: 0 Key : Hypervisor.Flags.SynicAvailable Value: 0 Key : Hypervisor.Flags.UseQpcBias Value: 0 Key : Hypervisor.Flags.Value Value: 536585 Key : Hypervisor.Flags.ValueHex Value: 83009 Key : Hypervisor.Flags.VpAssistPage Value: 1 Key : Hypervisor.Flags.VsmAvailable Value: 0 Key : Hypervisor.RootFlags.Value Value: 0 Key : Hypervisor.RootFlags.ValueHex Value: 0 Key : WER.OS.Branch Value: rs5_release Key : WER.OS.Version Value: 10.0.17763.1 BUGCHECK_CODE: 1e BUGCHECK_P1: ffffffffc0000096 BUGCHECK_P2: fffff804db200407 BUGCHECK_P3: 0 BUGCHECK_P4: 0 FILE_IN_CAB: MEMORY.DMP EXCEPTION_PARAMETER1: 0000000000000000 EXCEPTION_PARAMETER2: 0000000000000000 BLACKBOXBSD: 1 (!blackboxbsd) PROCESS_NAME: ASManagerService.exe TRAP_FRAME: ffffe782ff4a811c -- (.trap 0xffffe782ff4a811c) NOTE: The trap frame does not contain all registers. Some register values may be zeroed or incorrect. Unable to get program counter rax=0000000000000000 rbx=0000000000000000 rcx=0000000000000000 rdx=0000000000000000 rsi=0000000000000000 rdi=0000000000000000 rip=ff4a8280ffffe782 rsp=ff4a82a000000000 rbp=00060000ffffe782 r8=0000000000000000 r9=0000000000000000 r10=0000000000000000 r11=0000000000000000 r12=0000000000000000 r13=0000000000000000 r14=0000000000000000 r15=0000000000000000 iopl=0 nv up di pl nz na pe nc e782:e782 ?? ??? Resetting default scope IP_IN_FREE_BLOCK: 0 STACK_TEXT: ffff920e`9a9ac908 fffff802`6e0d4077 : 00000000`0000001e ffffffff`c0000096 fffff804`db200407 00000000`00000000 : nt!KeBugCheckEx ffff920e`9a9ac910 fffff802`6e06c102 : ffffe782`ff3c8a10 ffffbc89`00000000 ffffe782`ff4a811c fffff802`6deefd10 : nt!KiDispatchException+0x129ee7 ffff920e`9a9acfc0 fffff802`6e067885 : ffffe782`f9a02000 ffffbc89`00000190 ffff920e`00000000 ffff920e`9a9ad540 : nt!KiExceptionDispatch+0xc2 ffff920e`9a9ad1a0 fffff804`db200407 : ffffe782`ff0e94a0 00000000`00000000 00000000`00000000 ffffe782`fdf9b1b0 : nt!KiGeneralProtectionFault+0x305 ffff920e`9a9ad338 ffffe782`ff0e94a0 : 00000000`00000000 00000000`00000000 ffffe782`fdf9b1b0 fffff804`db209e91 : GVUSBD+0x407 ffff920e`9a9ad340 00000000`00000000 : 00000000`00000000 ffffe782`fdf9b1b0 fffff804`db209e91 ffffe782`fa0fef00 : 0xffffe782`ff0e94a0 SYMBOL_NAME: GVUSBD+407 MODULE_NAME: GVUSBD IMAGE_NAME: GVUSBD.sys STACK_COMMAND: .cxr; .ecxr ; kb BUCKET_ID_FUNC_OFFSET: 407 FAILURE_BUCKET_ID: 0x1E_C0000096_GVUSBD!unknown_function OS_VERSION: 10.0.17763.1 BUILDLAB_STR: rs5_release OSPLATFORM_TYPE: x64 OSNAME: Windows 10 FAILURE_ID_HASH: {e33840ed-d273-c482-6ab3-fda3f8b1b7cf} Followup: MachineOwner --------- -
@andsmith That's what I'm looking for. Which host CPU are you using? And if you don't mind, could you share with me the crash dump and the driver files being used (see Device Manager)? It might contain some sensitive information so if you have some concerns, feel free to share it via PM.
-
@dinhngtu said in 8.3 USB Passthrough - Win Server 2019 BSOD:
@andsmith That's what I'm looking for. Which host CPU are you using? And if you don't mind, could you share with me the crash dump and the driver files being used (see Device Manager)? It might contain some sensitive information so if you have some concerns, feel free to share it via PM.
Host Server is a Dell R760 with dual Intel(R) Xeon(R) Gold 5415+. We have a second server in the pool an older R740 with dual Intel(R) Xeon(R) Silver 4110 CPU @ 2.10GHz. I sent you a DM. The crash dump is 280mb.
-
@andsmith Could you try this command on the host:
xe vm-param-add uuid=... param-name=platform msr-relaxed=true(edit: it's
msr-relaxednotmsr_relaxed)Replace
...with your VM's UUID.You'll need to completely shut down the VM before running the command.
-
@dinhngtu said in 8.3 USB Passthrough - Win Server 2019 BSOD:
xe vm-param-add uuid=... param-name=platform msr_relaxed=true
This produced the same result.
-
@andsmith I misspelled the command, sorry. It should be
xe vm-param-add uuid=... param-name=platform msr-relaxed=true(Note the dash and not the underscore)
If your VM works afterwards, could you post the lines containing "RDMSR ... unimplemented" from the output of
xl dmesg? -
@dinhngtu said in 8.3 USB Passthrough - Win Server 2019 BSOD:
@andsmith I misspelled the command, sorry. It should be
xe vm-param-add uuid=... param-name=platform msr-relaxed=true(Note the dash and not the underscore)
If your VM works afterwards, could you post the lines containing "RDMSR ... unimplemented" from the output of
xl dmesg?Sweet, this worked! I searched the xl dmesg output, but didn't find any such line. So here is the whole thing:
__ __ _ _ _ _____ ____ \ \/ /___ _ __ | || | / |___ | ___| \ // _ \ '_ \ | || |_ | | / /|___ \ / \ __/ | | | |__ _|| | / /_ ___) | /_/\_\___|_| |_| |_|(_)_|/_/(_)____/ (XEN) [0000004693950393] Xen version 4.17.5-3 (mockbuild@[unknown]) (gcc (GCC) 11.2.1 20210728 (Red Hat 11.2.1-1)) debug=n Wed Oct 2 16:21:17 CEST 2024 (XEN) [0000004693951667] Latest ChangeSet: 430ce6cd9365, pq 326ba7419f1d (XEN) [0000004693952b35] build-id: 8dbf3a0a4e64db53bf7d322a2fde56a7a922f5e0 (XEN) [000000469395325d] Bootloader: GRUB 2.06 (XEN) [0000004693953a1b] Command line: dom0_mem=8192M,max:8192M watchdog ucode=scan dom0_max_vcpus=1-16 crashkernel=256M,below=4G console=vga vga=mode-0x0311 (XEN) [0000004693954657] Xen image load base address: 0x5a800000 (XEN) [0000004693954c4f] Video information: (XEN) [000000469395551d] VGA is graphics mode 1280x1024, 32 bpp (XEN) [0000004693955b8b] Disc information: (XEN) [000000469395619f] Found 0 MBR signatures (XEN) [0000004693956791] Found 2 EDD information structures (XEN) [0000004693958c67] CPU Vendor: Intel, Family 6 (0x6), Model 143 (0x8f), Stepping 8 (raw 000806f8) (XEN) [000000469395b8e7] Enabling Supervisor Shadow Stacks (XEN) [000000469395c14d] Enabling Indirect Branch Tracking (XEN) [000000469395c8af] - IBT disabled in UEFI Runtime Services (XEN) [00000046939607c9] EFI RAM map: (XEN) [000000469396116d] [0000000000000000, 000000000009ffff] (usable) (XEN) [0000004693961a9d] [00000000000a0000, 00000000000fffff] (reserved) (XEN) [000000469396240f] [0000000000100000, 000000004debbfff] (usable) (XEN) [0000004693962c91] [000000004debc000, 00000000506bbfff] (ACPI NVS) (XEN) [00000046939634d5] [00000000506bc000, 00000000641fdfff] (usable) (XEN) [0000004693963c7b] [00000000641fe000, 0000000074dfefff] (reserved) (XEN) [000000469396447d] [0000000074dff000, 00000000771fefff] (ACPI NVS) (XEN) [0000004693964c5d] [00000000771ff000, 00000000777fefff] (ACPI data) (XEN) [00000046939655a7] [00000000777ff000, 00000000777fffff] (usable) (XEN) [0000004693965d19] [0000000077800000, 000000008fffffff] (reserved) (XEN) [0000004693966499] [00000000fe010000, 00000000fe010fff] (reserved) (XEN) [0000004693966d41] [0000000100000000, 000000407fffffff] (usable) (XEN) [000000469506bab9] Kdump: 256MB (262144kB) at 0x3de00000 (XEN) [00000046950b30b9] ACPI: RSDP 777FE014, 0024 (r2 DELL ) (XEN) [00000046950b51b1] ACPI: XSDT 774F3188, 00E4 (r1 DELL PE_SC3 0 1000013) (XEN) [00000046950b6b7d] ACPI: FACP 777F6000, 0114 (r6 DELL PE_SC3 0 INTL 20091013) (XEN) [00000046950b84ed] ACPI: DSDT 776F5000, FBFCE (r2 DELL PE_SC3 3 INTL 20091013) (XEN) [00000046950b9639] ACPI: FACS 7653C000, 0040 (XEN) [00000046950ba2c9] ACPI: SSDT 777FB000, 131D (r2 INTEL RAS_ACPI 1 INTL 20210331) (XEN) [00000046950bb497] ACPI: SSDT 777FA000, 076E (r2 INTEL ADDRXLAT 1 INTL 20210331) (XEN) [00000046950bc427] ACPI: BERT 777F9000, 0030 (r1 DELL PE_SC3 1 INTL 1) (XEN) [00000046950bd3c9] ACPI: ERST 777F8000, 0230 (r1 DELL PE_SC3 1 INTL 1) (XEN) [00000046950be331] ACPI: MCEJ 777F7000, 0130 (r1 INTEL 1 INTL 100000D) (XEN) [00000046950bf257] ACPI: HPET 777F5000, 0038 (r1 DELL PE_SC3 1 INTL 20091013) (XEN) [00000046950c00df] ACPI: MCFG 777F4000, 003C (r1 DELL PE_SC3 1 INTL 20091013) (XEN) [00000046950c0ed5] ACPI: MIGT 777F3000, 0040 (r1 DELL PE_SC3 0 INTL 20091013) (XEN) [00000046950c1e65] ACPI: MSCT 777F2000, 0090 (r1 DELL PE_SC3 1 INTL 20091013) (XEN) [00000046950c2c17] ACPI: WSMT 777F1000, 0028 (r1 DELL PE_SC3 0 INTL 20091013) (XEN) [00000046950c3a07] ACPI: APIC 776F4000, 025E (r5 DELL PE_SC3 10182021 INTL 20091013) (XEN) [00000046950c49bf] ACPI: SRAT 776EC000, 7830 (r3 DELL PE_SC3 2 1000013) (XEN) [00000046950c5839] ACPI: SLIT 776EB000, 0030 (r1 DELL PE_SC3 2 1000013) (XEN) [00000046950c663b] ACPI: HMAT 776EA000, 0158 (r2 DELL PE_SC3 2 1000013) (XEN) [00000046950c748d] ACPI: OEM4 77562000, 187A51 (r2 INTEL CPU CST 3000 INTL 20210331) (XEN) [00000046950c85bd] ACPI: SSDT 774F8000, 69895 (r2 INTEL SSDT PM 4000 INTL 20210331) (XEN) [00000046950c94f7] ACPI: SSDT 774F7000, 0A1F (r2 DELL PE_SC3 0 INTL 20091013) (XEN) [00000046950ca451] ACPI: HEST 774F6000, 017C (r1 DELL PE_SC3 1 INTL 1) (XEN) [00000046950cb213] ACPI: SSDT 774F5000, 0623 (r2 DELL Tpm2Tabl 1000 INTL 20210331) (XEN) [00000046950cc1b9] ACPI: TPM2 774F4000, 004C (r4 DELL PE_SC3 2 1000013) (XEN) [00000046950ccf9f] ACPI: SSDT 777FD000, 085A (r2 DELL PE_SC3 2 DELL 1) (XEN) [00000046950cdd51] ACPI: NBFT 774F2000, 0122 (r1 DELL PE_SC3 0 1000013) (XEN) [00000046950ceb49] ACPI: DMAR 774F1000, 0370 (r1 DELL PE_SC3 1 INTL 20091013) (XEN) [0000004695135eaf] System RAM: 261657MB (267937404kB) (XEN) [00000046b947f713] SRAT: Node 0 PXM 0 [0000000000000000, 000000007fffffff] (XEN) [00000046b94804b9] SRAT: Node 0 PXM 0 [0000000100000000, 000000207fffffff] (XEN) [00000046b9480eb9] SRAT: Node 1 PXM 1 [0000002080000000, 000000407fffffff] (XEN) [00000046f67171e9] Domain heap initialised DMA width 32 bits (XEN) [00000046fc07a4b1] vesafb: framebuffer at 0x0000000094000000, mapped to 0xffff82c000201000, using 5120k, total 5120k (XEN) [00000046fc07b199] vesafb: mode is 1280x1024x32, linelength=5120, font 8x16 (XEN) [00000046fc07bdf7] vesafb: Truecolor: size=8:8:8:8, shift=24:16:8:0 (XEN) [0000004770f1c62f] SMBIOS 3.3 present. (XEN) [0000004770fea01b] XSM Framework v1.0.1 initialized (XEN) [00000047710ffd53] Initialising XSM SILO mode (XEN) [0000004771329d19] x2APIC mode is already enabled by BIOS. (XEN) [00000047714505cd] Using APIC driver x2apic_mixed (XEN) [00000047715ad32f] ACPI: PM-Timer IO Port: 0x508 (24 bits) (XEN) [00000047716bf507] ACPI: v5 SLEEP INFO: control[0:0], status[0:0] (XEN) [0000004771817ad9] ACPI: SLEEP INFO: pm1x_cnt[1:504,1:0], pm1x_evt[1:500,1:0] (XEN) [00000047719915bd] ACPI: 32/64X FACS address mismatch in FADT - 7653c000/0000000000000000, using 32 (XEN) [0000004771b5579d] ACPI: wakeup_vec[7653c00c], vec_size[20] (XEN) [0000004771e92ab5] ACPI: IOAPIC (id[0x08] address[0xfec00000] gsi_base[0]) (XEN) [00000047720b2595] IOAPIC[0]: apic_id 8, version 32, address 0xfec00000, GSI 0-119 (XEN) [0000004772270755] ACPI: INT_SRC_OVR (bus 0 bus_irq 0 global_irq 2 dfl dfl) (XEN) [0000004772431289] ACPI: INT_SRC_OVR (bus 0 bus_irq 9 global_irq 9 high level) (XEN) [0000004772674de5] ACPI: HPET id: 0x8086a701 base: 0xfed00000 (XEN) [0000004772821923] PCI: MCFG configuration 0: base 80000000 segment 0000 buses 00 - ff (XEN) [0000004772a39499] PCI: MCFG area at 80000000 reserved in E820 (XEN) [0000004772bbdfe9] PCI: Using MCFG for segment 0000 bus 00-ff (XEN) [0000004772dac69f] Xen ERST support is initialized. (XEN) [0000004772eec0ab] HEST: Table parsing has been initialized (XEN) [000000477303e971] Using ACPI (MADT) for SMP configuration information (XEN) [00000047731f83f1] SMP: Allowing 32 CPUs (0 hotplug CPUs) (XEN) [000000477339e105] IRQ limits: 120 GSI, 6536 MSI/MSI-X (XEN) [0000004776ce4dab] BSP microcode revision: 0x2b0005d2 (XEN) [0000004776e9fbcb] CPU0: invalid PERF_GLOBAL_CTRL: 0 adjusting to 0xff (XEN) [0000004776fef70f] CPU0: TSC: 25000000 Hz * 232 / 2 = 2900000000 Hz (XEN) [000000477716993f] CPU0: bus: 100 MHz base: 2900 MHz max: 4100 MHz (XEN) [000000477753723d] CPU0: 800 ... 2900 MHz (XEN) [00000047776dc6d5] xstate: size: 0xa88 and states: 0x2e7 (XEN) [00000047778131af] CPU0: Intel machine check reporting enabled (XEN) [000000477797bc0f] Unrecognised CPU model 0x8f - assuming vulnerable to LazyFPU (XEN) [0000004777ba13b9] Speculative mitigation facilities: (XEN) [0000004777d331b9] Hardware hints: RDCL_NO EIBRS RRSBA SKIP_L1DFL MDS_NO TAA_NO SBDR_SSDP_NO FBSDP_NO PSDP_NO GDS_NO RFDS_NO (XEN) [00000047780263ab] Hardware features: IBPB IBRS STIBP SSBD PSFD L1D_FLUSH MD_CLEAR TSX_CTRL (XEN) [00000047782464ff] Compiled-in support: INDIRECT_THUNK HARDEN_ARRAY HARDEN_BRANCH HARDEN_GUEST_ACCESS HARDEN_LOCK (XEN) [00000047784c6f7b] Xen settings: BTI-Thunk: JMP, SPEC_CTRL: IBRS+ STIBP+ SSBD- PSFD- BHI_DIS_S+ TSX+, Other: IBPB-ctxt BRANCH_HARDEN (XEN) [00000047787b5c69] Support for HVM VMs: MSR_SPEC_CTRL MSR_VIRT_SPEC_CTRL RSB EAGER_FPU (XEN) [00000047789d1829] Support for PV VMs: MSR_SPEC_CTRL EAGER_FPU (XEN) [0000004778b86fe1] XPTI (64-bit PV only): Dom0 disabled, DomU disabled (with PCID) (XEN) [0000004778dfaa31] PV L1TF shadowing: Dom0 disabled, DomU disabled (XEN) [0000004778fef76d] Using scheduler: SMP Credit Scheduler (credit) (XEN) [0000004781c92429] Platform timer is 25.000MHz HPET (XEN) [ 1.378435] Detected 2899.999 MHz processor. (XEN) [ 1.388276] EFI memory map: (XEN) [ 1.388514] 0000000000000-0000000000fff type=3 attr=000000000000000f (XEN) [ 1.389112] 0000000001000-0000000004fff type=2 attr=000000000000000f (XEN) [ 1.389708] 0000000005000-000000000ffff type=7 attr=000000000000000f (XEN) [ 1.390291] 0000000010000-0000000013fff type=3 attr=000000000000000f (XEN) [ 1.390874] 0000000014000-000000004afff type=7 attr=000000000000000f (XEN) [ 1.391549] 000000004b000-000000005afff type=2 attr=000000000000000f (XEN) [ 1.392174] 000000005b000-0000000086fff type=3 attr=000000000000000f (XEN) [ 1.392716] 0000000087000-000000008ffff type=4 attr=000000000000000f (XEN) [ 1.393264] 0000000090000-000000009ffff type=3 attr=000000000000000f (XEN) [ 1.393868] 0000000100000-0000000794fff type=2 attr=000000000000000f (XEN) [ 1.394460] 0000000795000-0000000bfffff type=7 attr=000000000000000f (XEN) [ 1.395085] 0000000c00000-0000000ffffff type=3 attr=000000000000000f (XEN) [ 1.395737] 0000001000000-00000024a3fff type=2 attr=000000000000000f (XEN) [ 1.396484] 00000024a4000-000002324bfff type=7 attr=000000000000000f (XEN) [ 1.397241] 000002324c000-00000371fffff type=1 attr=000000000000000f (XEN) [ 1.398089] 0000037200000-00000372fffff type=4 attr=000000000000000f (XEN) [ 1.398960] 0000037300000-000004c2bffff type=7 attr=000000000000000f (XEN) [ 1.399746] 000004c2c0000-000004c3d3fff type=1 attr=000000000000000f (XEN) [ 1.400657] 000004c3d4000-000004debbfff type=3 attr=000000000000000f (XEN) [ 1.401635] 000004debc000-00000506bbfff type=10 attr=000000000000000f (XEN) [ 1.418699] Setting RUNTIME attribute for 000004debc000-00000506bbfff (XEN) [ 1.434726] 00000506bc000-0000051ffcfff type=3 attr=000000000000000f (XEN) [ 1.450505] 0000051ffd000-00000521fffff type=4 attr=000000000000000f (XEN) [ 1.470268] 0000052200000-0000052267fff type=3 attr=000000000000000f (XEN) [ 1.488400] 0000052268000-0000052287fff type=4 attr=000000000000000f (XEN) [ 1.507214] 0000052288000-0000052309fff type=3 attr=000000000000000f (XEN) [ 1.526352] 000005230a000-0000052326fff type=4 attr=000000000000000f (XEN) [ 1.543590] 0000052327000-000005235afff type=3 attr=000000000000000f (XEN) [ 1.562588] 000005235b000-000005235bfff type=4 attr=000000000000000f (XEN) [ 1.581282] 000005235c000-000005235ffff type=3 attr=000000000000000f (XEN) [ 1.598584] 0000052360000-0000052396fff type=4 attr=000000000000000f (XEN) [ 1.615713] 0000052397000-00000523aefff type=3 attr=000000000000000f (XEN) [ 1.633370] 00000523af000-00000523c9fff type=4 attr=000000000000000f (XEN) [ 1.652247] 00000523ca000-00000523d0fff type=3 attr=000000000000000f (XEN) [ 1.668917] 00000523d1000-00000523e7fff type=4 attr=000000000000000f (XEN) [ 1.686545] 00000523e8000-0000052402fff type=3 attr=000000000000000f (XEN) [ 1.705380] 0000052403000-000005242dfff type=4 attr=000000000000000f (XEN) [ 1.725300] 000005242e000-000005243dfff type=3 attr=000000000000000f (XEN) [ 1.741681] 000005243e000-0000052d17fff type=4 attr=000000000000000f (XEN) [ 1.757121] 0000052d18000-0000052d22fff type=3 attr=000000000000000f (XEN) [ 1.772548] 0000052d23000-0000052d3cfff type=4 attr=000000000000000f (XEN) [ 1.788848] 0000052d3d000-0000052d48fff type=3 attr=000000000000000f (XEN) [ 1.806686] 0000052d49000-0000052d64fff type=4 attr=000000000000000f (XEN) [ 1.823536] 0000052d65000-0000052d95fff type=3 attr=000000000000000f (XEN) [ 1.840824] 0000052d96000-0000052dd6fff type=4 attr=000000000000000f (XEN) [ 1.858861] 0000052dd7000-0000052dd8fff type=3 attr=000000000000000f (XEN) [ 1.875619] 0000052dd9000-00000570d9fff type=4 attr=000000000000000f (XEN) [ 1.892683] 00000570da000-00000570e8fff type=3 attr=000000000000000f (XEN) [ 1.909471] 00000570e9000-00000570e9fff type=4 attr=000000000000000f (XEN) [ 1.925096] 00000570ea000-0000057116fff type=3 attr=000000000000000f (XEN) [ 1.941540] 0000057117000-00000571c0fff type=4 attr=000000000000000f (XEN) [ 1.957492] 00000571c1000-00000571c1fff type=2 attr=000000000000000f (XEN) [ 1.975048] 00000571c2000-00000571dffff type=3 attr=000000000000000f (XEN) [ 1.991642] 00000571e0000-00000571eafff type=4 attr=000000000000000f (XEN) [ 2.008069] 00000571eb000-00000571fdfff type=3 attr=000000000000000f (XEN) [ 2.023999] 00000571fe000-000005a9fffff type=7 attr=000000000000000f (XEN) [ 2.039571] 000005aa00000-000005b3fffff type=2 attr=000000000000000f (XEN) [ 2.056001] 000005b400000-000005bc24fff type=7 attr=000000000000000f (XEN) [ 2.072679] 000005bc25000-00000641fdfff type=4 attr=000000000000000f (XEN) [ 2.087838] 00000641fe000-00000645fdfff type=6 attr=800000000000000f (XEN) [ 2.103707] 00000645fe000-0000064dfdfff type=5 attr=800000000000000f (XEN) [ 2.119118] 0000064dfe000-0000074dfefff type=0 attr=000000000000000f (XEN) [ 2.137570] 0000074dff000-00000771fefff type=10 attr=000000000000000f (XEN) [ 2.153361] Setting RUNTIME attribute for 0000074dff000-00000771fefff (XEN) [ 2.168626] 00000771ff000-00000777fefff type=9 attr=000000000000000f (XEN) [ 2.185156] 00000777ff000-00000777fffff type=4 attr=000000000000000f (XEN) [ 2.200602] 0000100000000-000407fffffff type=7 attr=000000000000000f (XEN) [ 2.216274] 00000000a0000-00000000fffff type=0 attr=0000000000000000 (XEN) [ 2.232227] 0000077800000-0000077ffffff type=0 attr=0000000000000000 (XEN) [ 2.247423] 0000078000000-000007fffffff type=0 attr=0000000000000009 (XEN) [ 2.262021] 0000080000000-000008fffffff type=11 attr=8000000000000001 (XEN) [ 2.280292] 00000fe010000-00000fe010fff type=11 attr=8000000000000001 (XEN) [ 2.295163] alt table ffff82d0406a36b8 -> ffff82d0406b2e58 (XEN) [ 2.320912] Intel VT-d iommu 12 supported page sizes: 4kB, 2MB, 1GB (XEN) [ 2.335317] Intel VT-d iommu 11 supported page sizes: 4kB, 2MB, 1GB (XEN) [ 2.350660] Intel VT-d iommu 10 supported page sizes: 4kB, 2MB, 1GB (XEN) [ 2.366445] Intel VT-d iommu 9 supported page sizes: 4kB, 2MB, 1GB (XEN) [ 2.380589] Intel VT-d iommu 8 supported page sizes: 4kB, 2MB, 1GB (XEN) [ 2.396467] Intel VT-d iommu 7 supported page sizes: 4kB, 2MB, 1GB (XEN) [ 2.412889] Intel VT-d iommu 6 supported page sizes: 4kB, 2MB, 1GB (XEN) [ 2.428571] Intel VT-d iommu 5 supported page sizes: 4kB, 2MB, 1GB (XEN) [ 2.443744] Intel VT-d iommu 4 supported page sizes: 4kB, 2MB, 1GB (XEN) [ 2.459681] Intel VT-d iommu 3 supported page sizes: 4kB, 2MB, 1GB (XEN) [ 2.475423] Intel VT-d iommu 2 supported page sizes: 4kB, 2MB, 1GB (XEN) [ 2.491314] Intel VT-d iommu 1 supported page sizes: 4kB, 2MB, 1GB (XEN) [ 2.508744] Intel VT-d iommu 0 supported page sizes: 4kB, 2MB, 1GB (XEN) [ 2.524051] Intel VT-d iommu 13 supported page sizes: 4kB, 2MB, 1GB (XEN) [ 2.539590] Intel VT-d Snoop Control enabled. (XEN) [ 2.555276] Intel VT-d Dom0 DMA Passthrough not enabled. (XEN) [ 2.571181] Intel VT-d Queued Invalidation enabled. (XEN) [ 2.589660] Intel VT-d Interrupt Remapping enabled. (XEN) [ 2.605988] Intel VT-d Posted Interrupt not enabled. (XEN) [ 2.620523] Intel VT-d Shared EPT tables enabled. (XEN) [ 2.639064] I/O virtualisation enabled (XEN) [ 2.654550] - Dom0 mode: Relaxed (XEN) [ 2.669120] Interrupt remapping enabled (XEN) [ 2.683791] Enabled directed EOI with ioapic_ack_old on! (XEN) [ 2.700845] Enabling APIC mode. Using 1 I/O APICs (XEN) [ 2.722047] ENABLING IO-APIC IRQs (XEN) [ 2.735628] -> Using old ACK method (XEN) [ 2.749524] ..TIMER: vector=0xF0 apic1=0 pin1=2 apic2=-1 pin2=-1 (XEN) [ 3.677505] Defaulting to alternative key handling; send 'A' to switch to normal mode. (XEN) [ 3.693501] Allocated console ring of 128 KiB. (XEN) [ 3.709086] VMX: Supported advanced features: (XEN) [ 3.724997] - APIC MMIO access virtualisation (XEN) [ 3.739628] - APIC TPR shadow (XEN) [ 3.753488] - Extended Page Tables (EPT) (XEN) [ 3.768246] - Virtual-Processor Identifiers (VPID) (XEN) [ 3.784820] - Virtual NMI (XEN) [ 3.799495] - MSR direct-access bitmap (XEN) [ 3.813649] - Unrestricted Guest (XEN) [ 3.828341] - VMCS shadowing (XEN) [ 3.842369] - VM Functions (XEN) [ 3.855050] - Virtualisation Exceptions (XEN) [ 3.868443] - Page Modification Logging (XEN) [ 3.882016] - TSC Scaling (XEN) [ 3.897261] - Bus Lock Detection (XEN) [ 3.911781] - Notify VM Exit (XEN) [ 3.924642] - Virtualize SPEC_CTRL (XEN) [ 3.937029] HVM: ASIDs enabled. (XEN) [ 3.949954] HVM: VMX enabled (XEN) [ 3.963225] HVM: Hardware Assisted Paging (HAP) detected (XEN) [ 3.977009] HVM: HAP page sizes: 4kB, 2MB, 1GB (XEN) [ 3.990141] alt table ffff82d0406a36b8 -> ffff82d0406b2e58 (XEN) [ 4.005382] altcall: Optimised away 329 endbr64 instructions (XEN) [000000494bc303c5] CPU16: invalid PERF_GLOBAL_CTRL: 0 adjusting to 0xff (XEN) [ 4.048314] Brought up 32 CPUs (XEN) [ 4.061218] Testing NMI watchdog on all CPUs:ok (XEN) [ 4.334939] Scheduling granularity: cpu, 1 CPU per sched-resource (XEN) [ 4.347735] mcheck_poll: Machine check polling timer started. (XEN) [ 4.381323] NX (Execute Disable) protection active (XEN) [ 4.394476] d0 has maximum 1368 PIRQs (XEN) [ 4.407622] csched_alloc_domdata: setting dom 0 as the privileged domain (XEN) [ 4.421071] *** Building a PV Dom0 *** (XEN) [ 4.636874] Xen kernel: 64-bit, lsb (XEN) [ 4.650571] Dom0 kernel: 64-bit, PAE, lsb, paddr 0x1000000 -> 0x302c000 (XEN) [ 4.663505] PHYSICAL MEMORY ARRANGEMENT: (XEN) [ 4.676826] Dom0 alloc.: 0000004028000000->000000402c000000 (2075484 pages to be allocated) (XEN) [ 4.691897] Init. ramdisk: 000000407eb5c000->000000407ffffd69 (XEN) [ 4.705341] VIRTUAL MEMORY ARRANGEMENT: (XEN) [ 4.717775] Loaded kernel: ffffffff81000000->ffffffff8302c000 (XEN) [ 4.733502] Phys-Mach map: 0000008000000000->0000008001000000 (XEN) [ 4.747489] Start info: ffffffff8302c000->ffffffff8302c4b8 (XEN) [ 4.760816] Page tables: ffffffff8302d000->ffffffff8304a000 (XEN) [ 4.773359] Boot stack: ffffffff8304a000->ffffffff8304b000 (XEN) [ 4.788083] TOTAL: ffffffff80000000->ffffffff83400000 (XEN) [ 4.802269] ENTRY ADDRESS: ffffffff8242b180 (XEN) [ 4.815696] Dom0 has maximum 16 VCPUs (XEN) [ 4.896093] Initial low memory virq threshold set at 0x4000 pages. (XEN) [ 4.910548] Scrubbing Free RAM in background (XEN) [ 4.928442] Std. Loglevel: Errors, warnings and info (XEN) [ 4.942718] Guest Loglevel: Nothing (Rate-limited: Errors and warnings) (XEN) [ 4.959482] Xen is relinquishing VGA console. (XEN) [ 5.015409] *** Serial input to DOM0 (type 'CTRL-a' three times to switch input) (XEN) [ 5.015609] Freed 2048kB init memory -
@andsmith windbg is also a regular win32 app and is included in any recent windows SDK. Here: https://developer.microsoft.com/en-us/windows/downloads/windows-sdk/
You just need windbg so deselect all the other crap.
Hello! It looks like you're interested in this conversation, but you don't have an account yet.
Getting fed up of having to scroll through the same posts each visit? When you register for an account, you'll always come back to exactly where you were before, and choose to be notified of new replies (either via email, or push notification). You'll also be able to save bookmarks and upvote posts to show your appreciation to other community members.
With your input, this post could be even better 💗
Register Login