XOCE Integration with OpenLDAP
-
@borzel, I made the adjustment, now a new error appears.
plugin.test { "id": "auth-ldap", "data": { "username": "marcos", "password": "* obfuscated *" } } { "message": "could not authenticate user", "name": "Error", "stack": "Error: could not authenticate user at _authenticate.then.result (/opt/xen-orchestra/packages/xo-server-auth-ldap/src/index.js:172:14) at tryCatcher (/opt/xen-orchestra/node_modules/bluebird/js/release/util.js:16:23) at Promise._settlePromiseFromHandler (/opt/xen-orchestra/node_modules/bluebird/js/release/promise.js:517:31) at Promise._settlePromise (/opt/xen-orchestra/node_modules/bluebird/js/release/promise.js:574:18) at Promise._settlePromise0 (/opt/xen-orchestra/node_modules/bluebird/js/release/promise.js:619:10) at Promise._settlePromises (/opt/xen-orchestra/node_modules/bluebird/js/release/promise.js:699:18) at _drainQueueStep (/opt/xen-orchestra/node_modules/bluebird/js/release/async.js:138:12) at _drainQueue (/opt/xen-orchestra/node_modules/bluebird/js/release/async.js:131:9) at Async._drainQueues (/opt/xen-orchestra/node_modules/bluebird/js/release/async.js:147:5) at Immediate.Async.drainQueues (/opt/xen-orchestra/node_modules/bluebird/js/release/async.js:17:14) at runCallback (timers.js:810:20) at tryOnImmediate (timers.js:768:5) at processImmediate [as _immediateCallback] (timers.js:745:5)" }Best regards,
Wesley Santos -
@wesleylc1 at this stage I'm out

@olivierlambert or @julien-f maybe can help.
-
@borzel, thank you.
-
Hello, I was able to login with my ldap login, but I would like to specify a ldap user group.
Best regards,
Wesley Santos -
So use a filter with the group you want.
-
Changes made, as below.
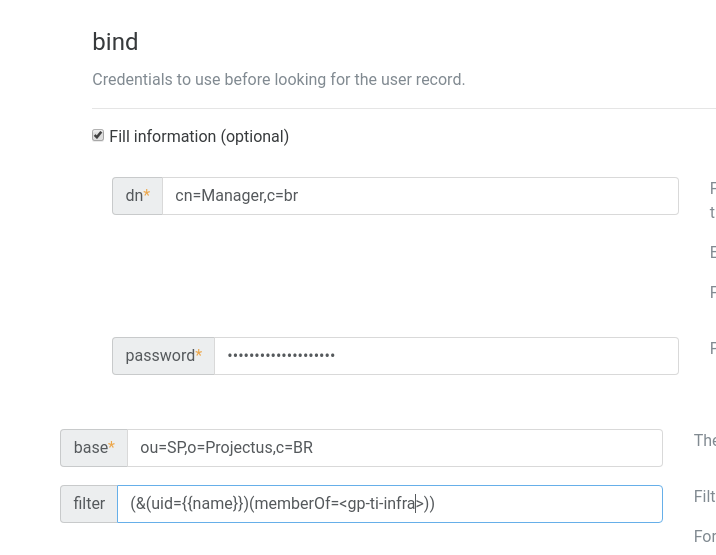
Best regards,
Wesley Santos -
Why the group name is between
< >? -
I made the changes, but I continue with errors.
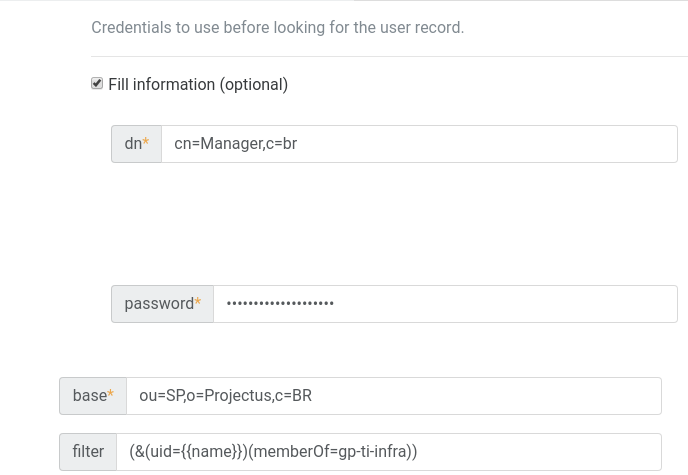
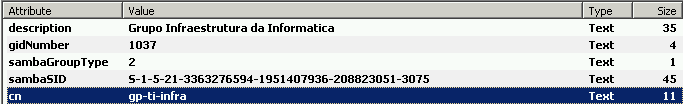
Group settings in "OpenLDAP".
plugin.test { "id": "auth-ldap", "data": { "username": "ws02", "password": "* obfuscated *" } } { "message": "could not authenticate user", "name": "Error", "stack": "Error: could not authenticate user at _authenticate.then.result (/opt/xen-orchestra/packages/xo-server-auth-ldap/src/index.js:172:14) at tryCatcher (/opt/xen-orchestra/node_modules/bluebird/js/release/util.js:16:23) at Promise._settlePromiseFromHandler (/opt/xen-orchestra/node_modules/bluebird/js/release/promise.js:517:31) at Promise._settlePromise (/opt/xen-orchestra/node_modules/bluebird/js/release/promise.js:574:18) at Promise._settlePromise0 (/opt/xen-orchestra/node_modules/bluebird/js/release/promise.js:619:10) at Promise._settlePromises (/opt/xen-orchestra/node_modules/bluebird/js/release/promise.js:699:18) at _drainQueueStep (/opt/xen-orchestra/node_modules/bluebird/js/release/async.js:138:12) at _drainQueue (/opt/xen-orchestra/node_modules/bluebird/js/release/async.js:131:9) at Async._drainQueues (/opt/xen-orchestra/node_modules/bluebird/js/release/async.js:147:5) at Immediate.Async.drainQueues (/opt/xen-orchestra/node_modules/bluebird/js/release/async.js:17:14) at runCallback (timers.js:810:20) at tryOnImmediate (timers.js:768:5) at processImmediate [as _immediateCallback] (timers.js:745:5)" }Best regards,
Wesley Santos -
I don't think that's the right syntax. But it's not a XO issue, it's a LDAP setting issue. Check what filter would work with your LDAP server, and it will work.
-
@wesleylc1 maybe the
memberOf=needs a LDAP-Value likeCN=blabla,OU=yadayada,DC=whatever? -
@olivierlambert
I think the error is related to the attributes of "OpenLDAP", but I'm not sure how to filter. -
You need to find/read documentation on LDAP filter for your server. Then it will work

-
Dear, is it possible to search with the "group and users" option?
Best regards,
Wesley Santos -
@wesleylc1 As @olivierlambert said, this is an LDAP config issue, you need to know the structure of your LDAP server.
The
auth-ldapplugin comes with a CLI which is useful to test various configuration and figure out what is wrong:$ /usr/local/lib/node_modules/xo-server-auth-ldap/dist/test-cli.js ? uri -
Dear @julien-f ,
I was able to perform the integration with "OpenLDAP", but I can not apply the filter using "" memberOf "", I could identify, the filter does not occur because my "LDAP" uses old parameters, filters using the "memberUid" attribute. You have some examples of how I can apply to filter group users with the "memberUid" attribute.
Best regards,
Wesley Santos -
@wesleylc1 It really depends of the structure of your LDAP server.
I've just committed a new version of the plugin which makes the test CLI displays the matched entry on success, this helps figuring out what should be put in the filter field.
Example:
$ xo-server-auth-ldap ? uri ldap://ldap.company.net ? fill optional certificateAuthorities? No ? fill optional checkCertificate? No ? fill optional bind? No ? base ou=people,dc=company,dc=net ? fill optional filter? No configuration saved in ./ldap.cache.conf ? Username john.smith ? Password [hidden] searching for entries... . 1 entries found attempting to bind as uid=john.smith,ou=people,dc=company,dc=net successfully bound as uid=john.smith,ou=people,dc=company,dc=net => john.smith authenticated { "messageID": 1, "protocolOp": "SearchEntry", "objectName": "uid=john.smith,ou=people,dc=company,dc=net", "attributes": [ { "type": "cn", "vals": [ "John Smith" ] }, { "type": "gidNumber", "vals": [ "10000" ] }, { "type": "givenName", "vals": [ "John" ] }, { "type": "homeDirectory", "vals": [ "/home/john.smith" ] }, { "type": "initials", "vals": [ "JSH" ] }, { "type": "loginShell", "vals": [ "/bin/bash" ] }, { "type": "mail", "vals": [ "john.smith@company.net" ] }, { "type": "objectClass", "vals": [ "posixAccount", "inetOrgPerson", "organizationalPerson", "person" ] }, { "type": "sn", "vals": [ "Smith" ] }, { "type": "uid", "vals": [ "john.smith" ] }, { "type": "uidNumber", "vals": [ "10000" ] } ], "controls": [] } -
@julien-f With this test option would be perfect to find out which filter should I use, how do I update to this version of the plugin?
? uri 192.168.XX.XX ? fill optional certificateAuthorities? No ? fill optional checkCertificate? No ? fill optional bind? No ? base ou=BH,o=PRJ,c=BR ? fill optional filter? No configuration saved in ./ldap.cache.conf ? Username cn=adm,c=br ? Password [hidden] ✖ 192.168.xx.xx is an invalid LDAP url (protocol) TypeError: 192.168.XX.XX is an invalid LDAP url (protocol) at Object.parse (/opt/xen-orchestra/node_modules/ldapjs/lib/url.js:16:13) at new Client (/opt/xen-orchestra/node_modules/ldapjs/lib/client/client.js:310:16) at createClient (/opt/xen-orchestra/node_modules/ldapjs/lib/client/index.js:54:12) at /opt/xen-orchestra/packages/xo-server-auth-ldap/dist/index.js:204:47 at Generator.next (<anonymous>) at asyncGeneratorStep (/opt/xen-orchestra/packages/xo-server-auth-ldap/dist/index.js:24:103) at _next (/opt/xen-orchestra/packages/xo-server-auth-ldap/dist/index.js:26:194) at /opt/xen-orchestra/packages/xo-server-auth-ldap/dist/index.js:26:364 at new Promise (<anonymous>) at /opt/xen-orchestra/packages/xo-server-auth-ldap/dist/index.js:26:97Best regards,
Wesley Santos -
It depends how you installed it, unfortunately I cannot help you for this.
Once you've upgrade to the latest version, use the default filter to authenticate the user and then you will see what fields it contains, then you will be able to write the correct filter.
-
I performed the installation through the link below.
https://github.com/Jarli01/xenorchestra_installer
the version of the updated plugin is already available in the Jarli repositories?
Best regards,
Wesley Santos -
@julien-f Can you list what types of filters are supported by the plugin?
Hello! It looks like you're interested in this conversation, but you don't have an account yet.
Getting fed up of having to scroll through the same posts each visit? When you register for an account, you'll always come back to exactly where you were before, and choose to be notified of new replies (either via email, or push notification). You'll also be able to save bookmarks and upvote posts to show your appreciation to other community members.
With your input, this post could be even better 💗
Register Login