XOCE Integration with OpenLDAP
-
@julien-f How can I download the new version of the plugin, according to the output below, I can not automatically query the filters through the script "/test-cli.js".
? uri ldap://192.168.xx.xx ? fill optional certificateAuthorities? No ? fill optional checkCertificate? No ? fill optional bind? Yes ? bind > dn cn=admin,c=br ? bind > password XXXX ? base ou=XX,o=PRJ,c=BR ? fill optional filter? Yes ? filter (&(cn=gp-ti-infra)(memberUID={{name}})) configuration saved in ./ldap.cache.conf ? Username user01 ? Password [hidden] attempting to bind with as cn=admin,c=br... successfully bound as cn=admin,c=br searching for entries... . 1 entries found attempting to bind as cn=gp-ti-test,ou=Grupos,ou=XX,o=PRJ,c=BR failed to bind as cn=gp-ti-test,ou=Grupos,ou=XX,o=PRJ,c=BR: Invalid Credentials could not authenticate user1 -
@wesleylc1 For the upgrade, you need to ask the people behind the install script you used.
Concerning the output, it will only show the entry if the authentication was successful, that's why you need to start by using the default filter.
-
The default filter is (uid = {{name}})?
-
@julien-f the filter "(& (cn = gp-ti-test) (memberUID = {{name}}))" is to release access to users of a group but "bind as" is not being mounted as it should
? uri ldap://192.168.XX.XX ? fill optional certificateAuthorities? No ? fill optional checkCertificate? No ? fill optional bind? Yes ? bind > dn cn=adm,c=br ? bind > password ***** ? base ou=BH,o=PRJ,c=BR ? fill optional filter? Yes ? filter (&(cn=gp-ti-teste)(memberUID={{name}})) configuration saved in ./ldap.cache.conf ? Username user1 ? Password [hidden] attempting to bind with as cn=adm,c=br... successfully bound as cn=adm,c=br searching for entries... . 1 entries found attempting to bind as cn=gp-ti-teste,ou=Grupos,ou=BH,o=PRJ,c=BR failed to bind as cn=gp-ti-teste,ou=Grupos,ou=BH,o=PRJ,c=BR: Invalid Credentials could not authenticate user1Best regards,
Wesley Santos -
This does not appear to be an XO issue, more a config issue, I don't have much time to investigate this any further, maybe the rest of the community can help on this.
-
thank you.
-
you using openldap or trying to integrate with an actual MSAD ?
My settings (to connect to MSAD)
URI: ldap://adress.to.my.dc
bind dn: myUserToConnectToDC@domain.com
pass: password.to.user.in.bind.dn
base: dc=domain,dc=com (because i've had set up restrictions on my user, thats why i pointed the full catalogue)
filter: (sAMAccountName={{name}})try those

-
@Kudzu he uses OpenLDAP, as he said in this thread earlier.
-
Any news in this issue?
@wesleylc1 have You figured out how the filter should looks like? -
Hi @redy it's not an "issue", it's a configuration for the user. Our LDAP plugin is working

-
@olivierlambert Plugin working for one user only in my environment, and only one user was synchronized, the one credential I've configured in plugin but not others. Second thing when I use filter (&(uid={{name}})(memberOf=access_xo)) and try to test I'he got an error about wrong credentials even if my LDAP user is a member of this group.
Test pass only when filter is setup to (uid={{name}}) and only ldap_sync user is synced.
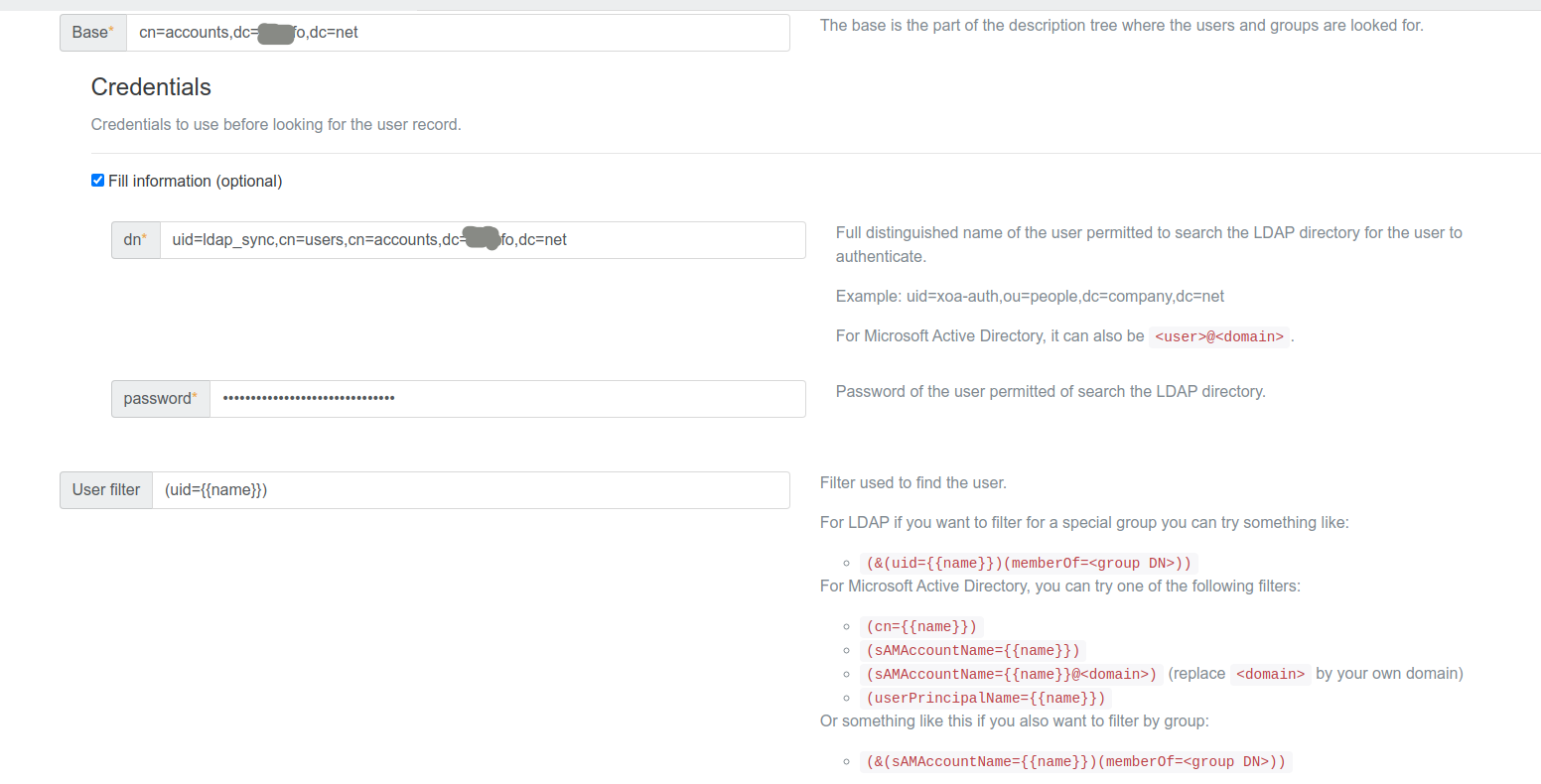
-
That's a configuration issue, not a bug

On our own OpenLDAP here at Vates, it works. And it's the same for a lot of customers around the world. So double check your LDAP config (from XO or your directory) to find the problem.
It's hard for us to assist because there's no universal way of using an LDAP directory. To use this plugin properly, you need to have enough LDAP skills (and yes, LDAP requires some skills, I don't really like it myself because I find it a bit overcomplicated).
Anyway, double check your base, that you are using the right user for binding and so on.
-
Also, the user will be created only on first connection. Maybe you are thinking about the plugin in a way that's not how it behave.
Hello! It looks like you're interested in this conversation, but you don't have an account yet.
Getting fed up of having to scroll through the same posts each visit? When you register for an account, you'll always come back to exactly where you were before, and choose to be notified of new replies (either via email, or push notification). You'll also be able to save bookmarks and upvote posts to show your appreciation to other community members.
With your input, this post could be even better 💗
Register Login