Citrix Hypervisor 8.1 released
-
I was able to download the PDF with the documentation of 8.1. Happy for Xen 4.13 and WLB integrated with XenCenter...
But I was sad that they didn't evolve with GFS2 and removed DMC.
-
- Xen 4.13 in a RC version because it's not yet released

- You have a WLB-like in Xen Orchestra since a while now

- DMC removed? As a feature in some edition or everywhere?
- Xen 4.13 in a RC version because it's not yet released
-
@olivierlambert
Notes:
• Dynamic Memory Control is deprecated in Citrix Hypervisor 8.1 and will be removed in a
future release.See file.. https://gofile.io/?c=xRuFy8 (citrix-hypervisor-8.1.pdf)
-
Interesting... I wanted to post it as news, but it popped up as existing (similar...) - so it seems it's officially out now!
I don't see what Xen 4.13 brings to us. We're still on the LTSR track and wait for Vates to get official support by HPE.
They say things about storage performance improvements:
Multipage support is now available in non-GFS2 SRs for better storage performance.I'm curious about what people will report back - and when XCP 8.1 comes out.

-
@cg Yeah I'll reping HPE again.
-
I'm honestly looking forward to the removal of DMC. It has caused more issues for me than it offers benefits

I can see how this can cause problems for those who relied on it to over subscribe memory resources though.Also noticed they are deprecating the vSwitch Controller.

@olivierlambert do you and the team have any plans to offer a solution that may fulfill some of the missing functions from the vSwitch Controller like VM Access Control List (ACL) rules or any other types of ACLs for network traffic as part of the SDN plug-in or some other plug-in?
-
@GHW We don't have plan because we don't know what people want more than what we released in our SDN controller plugin. Feel free to share specs on what you need so we can review how long it could take to make it real.
-
Do you mean that Dynamic Memory (balooning) won't be available in XCP-ng 8.1?
-
@GHW I agree ... they failed to apply the same level of reliability during live migration as VMWare has ...
-
I saw, they announced that it will become obsolete, but they did not announce whether there will be a replacement or not.
We will have to wait for the next chapters.They might well say what the possible future plans are.
-
@olivierlambert at this time the only feature that I was interested in is the VM level access control list function
I was working on a plan to build a pool with an internal network and an external network connected directly to the Internet. I wanted a central solution for controlling IP and port access for VMs on the external network and after much research and planning I ended with the vSwitch controller despite its annoying dependency on IE.
The main reason I was planning to settle with the vSwitch controller was because of its ability to enforce the access control list policy. The other ideas I entertained were:
-
Set iptable rules within the VM....but if a user changes the rule set or disables the firewall then it no longer matches the approved/required policy
-
Use and automation tool like Ansible....but it also faces an issue if the user changes the rule set or disables the firewall within the VM
-
Searched for paid solutions(software and/or SaaS) that could achieve this task....I did find one solution that claimed to offer just that but it seems the company behind it is no longer active. I also found other solutions that offer it as part of a bigger $100K type solution that is currently out of scope budget wise
In the end I was planning to settle with the vSwitch controller because I found no other viable solution and it can enforce the rule set/policy outside of the VM's control space....until I saw the plans to deprecate the feature

-
-
I'm not happy to see DMC dropping, but even more removal of "VSS and quiesced snapshots" is sad.
It's probably one more step from general Hypervisor solution to VDI, as it's not really important there, but if you have DB servers etc... -
-
@olivierlambert the idea of iptables for the VM, Ansible etc. were just other options I looked into as alternatives because DVSC was not my first choice option due to its limitations of only supporting IE and the "heavy" DVSC appliance
The specific feature that I wanted to use is the "Access Control policies" to achieve something similar to AWS security groups. https://docs.citrix.com/en-us/citrix-hypervisor/vswitch-controller/virtual-network-visibility.html#set-up-access-control-policies
-
@GHW @olivierlambert The Access Control lists in the DVSC instance was easily one of its most powerful and useful features. It essentially turned the DVS into an actual port-level security capable virtual switch. If it had full-featured routing, it would have been a very nifty solution to layer 3 in the virtual network space without having to run an entirely different appliance to achieve that capability. Perhaps that is something that the SDN could do at some point? (become a layer 3 capable switch with security access control)
-
Sadly I have no DVSC knowledge myself, so it would be great if you are able to explain in a kind of simple "high level specification" (eh "doing this in the UI with a screenshot, it does that") in a Github issue for SDN plugin, we might implement it on our side

-
So does the removal of the DMC mean that we wont be able to over-commit memory anymore?
Regards,
Marty -
@olivierlambert said in Citrix Hypervisor 8.1 released:
Sadly I have no DVSC knowledge myself, so it would be great if you are able to explain in a kind of simple "high level specification" (eh "doing this in the UI with a screenshot, it does that") in a Github issue for SDN plugin, we might implement it on our side

A bit of good news is that the DVSC works out of the box with XCP-ng 8.0. Though I have not tested it in conjunction with the SDN plug-in.
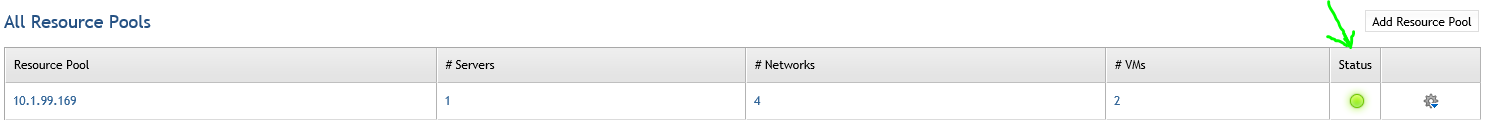
After importing the DVSC and adding it to the resource pool:
.1) Select the VM you want to apply security ACLs to
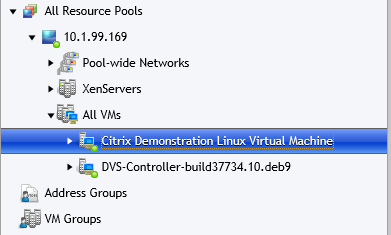
.2) Select "Access Control" and here you can create a network ACL policy to control traffic to and from the VM (by default there are no restrictions)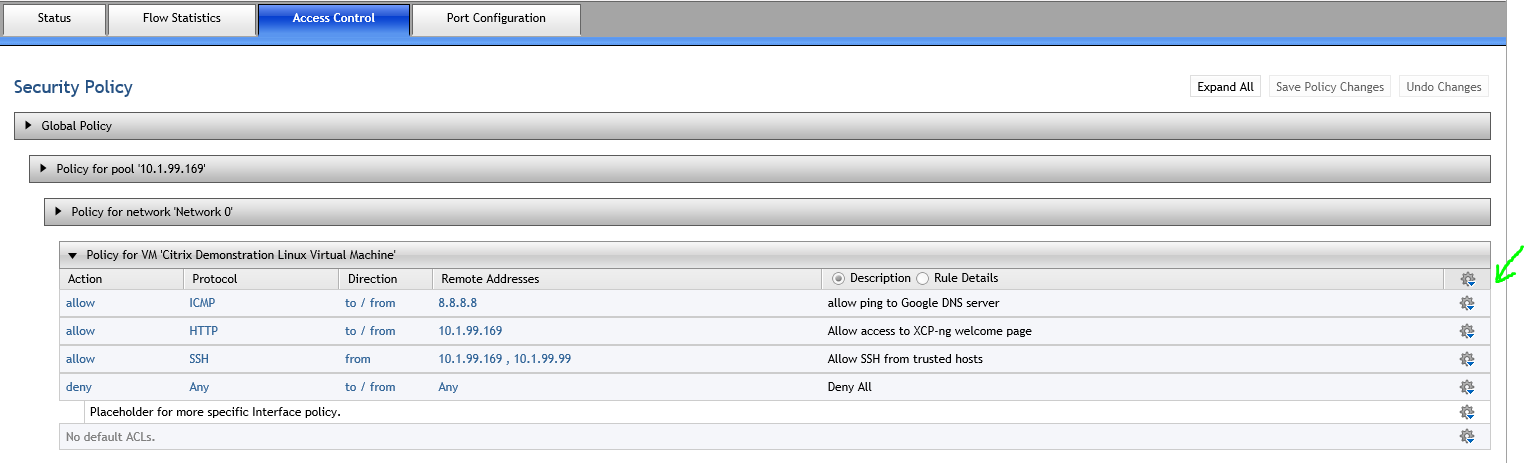
.3) Apply your desired network security policy to the VM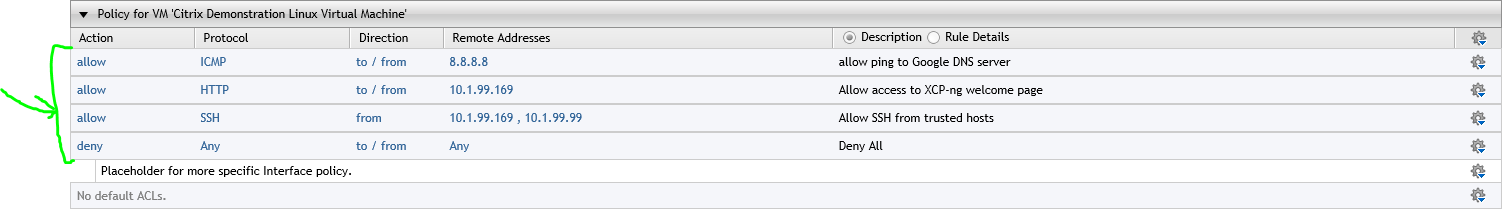
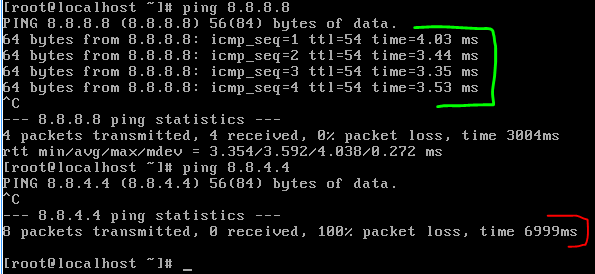
Results
Allows ping to 8.8.8.8 but blocks ping to 8.8.4.4 since it is not allowed in ACL policy
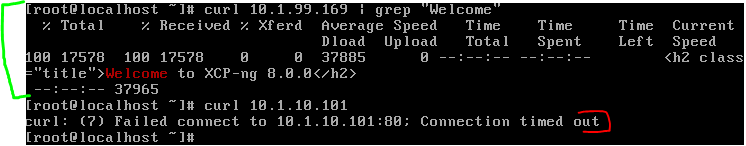
Allows access to HTTP web server as defined in the the VM network ACL policy and blocks access to the other
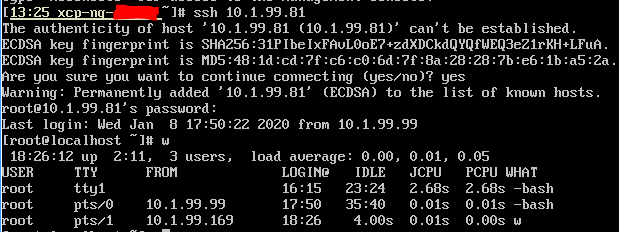
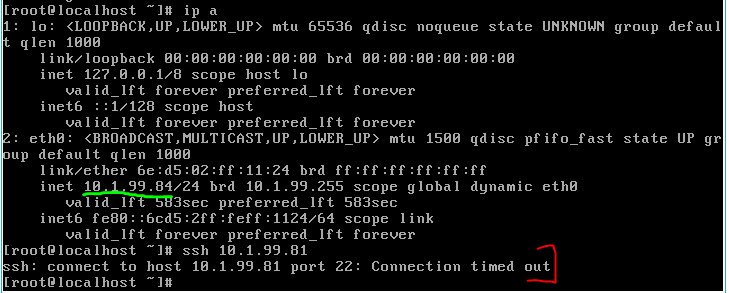
Restricts SSH access to trusted hosts
-
Thanks I'm pinging @BenjiReis who built the SDN plugin

-
@olivierlambert thanks

Hello! It looks like you're interested in this conversation, but you don't have an account yet.
Getting fed up of having to scroll through the same posts each visit? When you register for an account, you'll always come back to exactly where you were before, and choose to be notified of new replies (either via email, or push notification). You'll also be able to save bookmarks and upvote posts to show your appreciation to other community members.
With your input, this post could be even better 💗
Register Login