SAML Auth with Azure AD
-
@Mathieu yes indeed, I worked on this with @pierrebrunet PR https://github.com/vatesfr/xen-orchestra/pull/9042
Do you have any logs inxo-serverservice? -
@Mathieu Hi, you need to be sure to have signed assertion and signed response because only one won't be enough.
We have updated the doc when you saw the impact. Sorry for the inconvenience:
https://github.com/vatesfr/xen-orchestra/pull/9084/files#diff-6319d6b750c3bdbca61a9d9a1577a8aa4fa3a8a37764b91aef4672f69403baa4R221 -
Hello,
I've updated the cert with signed assertion and response

I also tried with a brand new certificate.
Unfortunately, login is still failing.
From xo-server:
Oct 09 08:11:17 xo-ce xo-server[272092]: Error: SAML assertion audience mismatch. Expected: 1671ff50-10e1-4a02-a0c5-4ed298898281 Received: https://XO_DNS_RECORD/ Oct 09 08:11:17 xo-ce xo-server[272092]: at /opt/xo/xo-builds/xen-orchestra-202510090759/node_modules/@node-saml/node-saml/src/saml.ts:1264:18 Oct 09 08:11:17 xo-ce xo-server[272092]: at Array.map (<anonymous>) Oct 09 08:11:17 xo-ce xo-server[272092]: at SAML.checkAudienceValidityError (/opt/xo/xo-builds/xen-orchestra-202510090759/node_modules/@node-saml/node-saml/src/saml.ts:1259:8) Oct 09 08:11:17 xo-ce xo-server[272092]: at SAML.processValidlySignedAssertionAsync (/opt/xo/xo-builds/xen-orchestra-202510090759/node_modules/@node-saml/node-saml/src/saml.ts:1151:32) Oct 09 08:11:17 xo-ce xo-server[272092]: at SAML.validatePostResponseAsync (/opt/xo/xo-builds/xen-orchestra-202510090759/node_modules/@node-saml/node-saml/src/saml.ts:808:16)And here is the plug-in configuration:
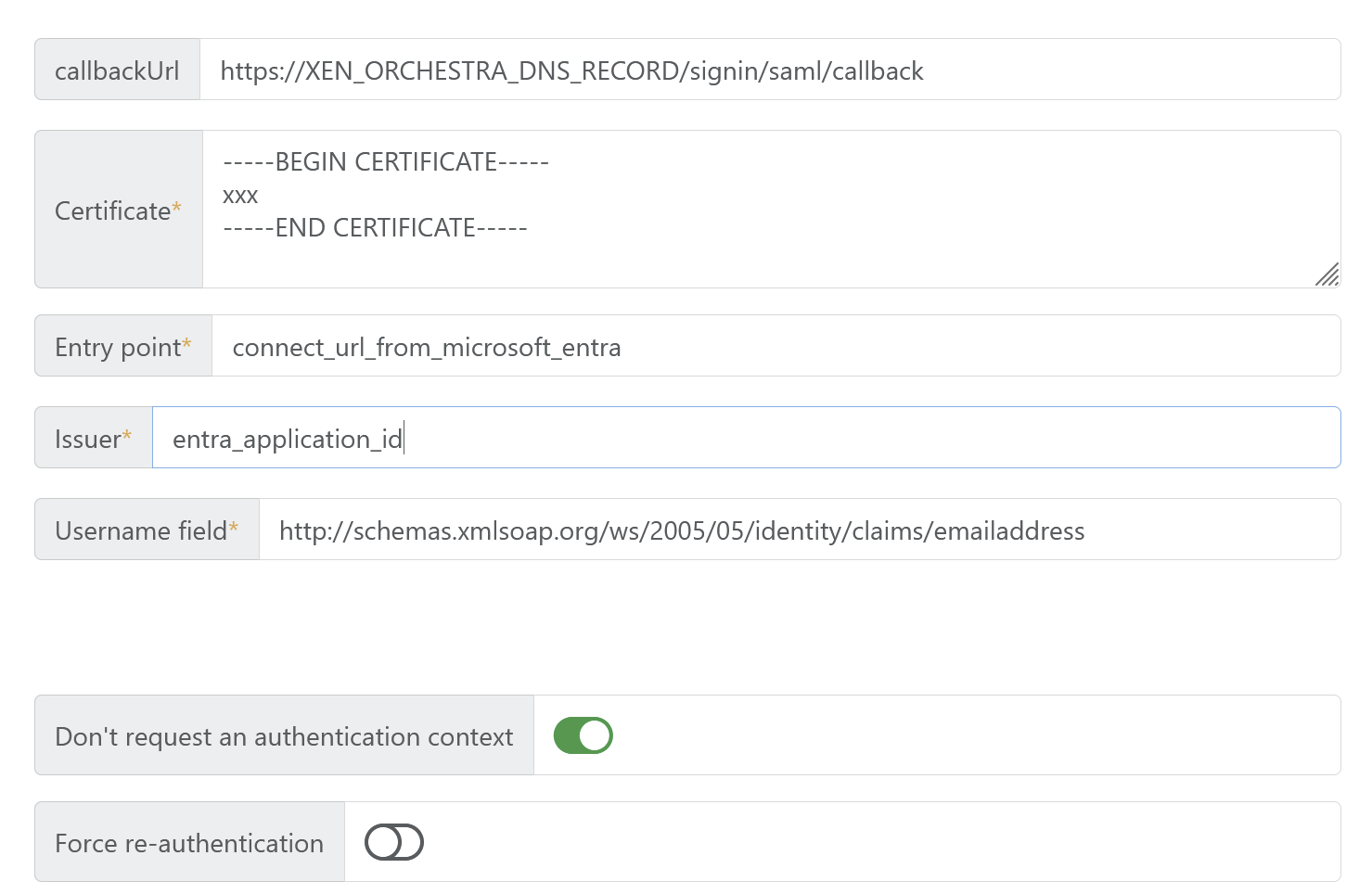
I'm not expert at all in SAML, sorry not being able to debug deeper.
-
@Mathieu Hello, can you show us your plugin configuration (without the certificate for security purpose) please?
Edit: thank you!
-
@pierrebrunet Just posted it above
-
@Mathieu Hi, do you use XO from source or do you have an XOA license? Just to know how to help you more confortably
-
@pierrebrunet
XO from source, commit 1ee07 from today. -
@Mathieu Thanks to your help, we are deploying a patch with config update and control over document and assertion signatures
https://github.com/vatesfr/xen-orchestra/pull/9093 -
@Mathieu Hi,
We merged the PR linked above with new options. If you have time, can you confirm it is working for you?
It will fix the audience error and let you choose if you want to sign responses and assertions. -
@pierrebrunet
I'm jumping in here as well. Reporting that the PR fixes it for Google Workspace as well!
However, the checkbox in GW is called "Signed response".
No further adjustments of the plugin itself was needed. -
@probain Hi,
Great!! Can you confirm the checkbox is in the Service Provider Details window? It is to enhance the doc part about SAML. -
@pierrebrunet
For Google Workspace:
Yes it is in the "Service Provider details"-section: See screenshot for example
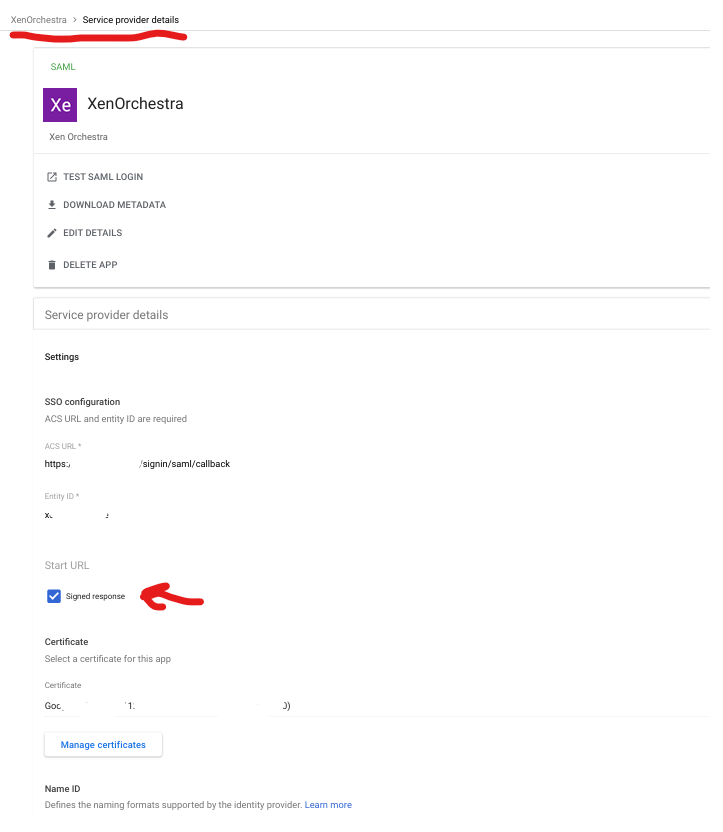
Edit: Removed doubled screenshot
-
@probain Thank you!
-
 O olivierlambert marked this topic as a question on
O olivierlambert marked this topic as a question on
-
 O olivierlambert has marked this topic as solved on
O olivierlambert has marked this topic as solved on
-
@pierrebrunet
Hello Pierre,Sorry for that late response, but yes, latest version is working fine and has solved the issue.
Thanks for the fix.
-
@pierrebrunet Are you aware if there is an official guide on how to use this with AzureAD ?
-
@TheNorthernLight I think this one is the most accurate: https://help.vates.tech/kb/en-us/48-plugins/162-saml-azure-guide
I've followed it and it worked, however there's two caveats:
- You need to use XOA 5.112, which is on the latest channel as today and not the stable channel.
- You need to Sign SAML response and assertion. To do that, Go to Microsoft Entra ID → Enterprise applications → Xen Orchestra → Single sign-on → SAML.
After those settings I could login with Azure ID / Entra ID / Whatever Microsoft calls today.
-
@olivierlambert can we report documentation issues or can we contribute to docs? I would fix myself if I can.
-
@ferrao Hey thanks, yes you are welcome to send a PR to improve the docs. It is based on Docusaurus, it is in the
docsdirectory in https://github.com/vatesfr/xen-orchestra/tree/master/docs. Then pages are in the 2nd leveldocsdirectory. -
On the bottom of each documentation page, there's an "Edit this page" link you can use to contribute

-
@olivierlambert
Just to add another weird case of this situation I tell you my SAML-auth-adventures.I have just migrated a week ago from XOCE to XOA paid support this week and all the process was fine except the auth with the saml plugin.
The commit I had in XOCE was [XO 5d92f - Master 3f604]. I compiled it the first week of this november so it wasn't very outdated.We use the MSEntraID SAML authentication and it was working fine in XOCE since at least one year ago.
Mi process was like this:
-
First, I installed XOA and imported the configuration from my old XOCE. Everything was fine and all was imported succesfully (backups, users, acls, etc.), including my plugin configurations.
Note that I reused the https server certificate/private key and used the same IP and the same DNS (beacuse I turned off my XOCE before starting XOA). -
Everything was working fine except the saml auth plugin. I had the same "Internal server error" problem.
I looked at the xo-server logs and the error was "invalid document signature" so, as Olivier said, we changed the configuration in MSEntraID to set the "Sign SAML response and assertion" on. -
Once we changed the configuration I thought the plugin would work again, but surprisingly not. If I try again SAML validation i still got the "Internal server error".
When i checked again the xo-server logs I saw ahother exception, this time with the error "SAML assertion audience mismatch" and a reference to the issuer configuration of the plugin.
The exact error I got from xo-server logs using "journalctl -u xo-server -f -n 50" was: "xoa xo-server[2370]: Error: SAML assertion audience mismatch. Expected: <id-of-MSEntraID-xo-validation> Received: spn:<id-of-MSEntraID-xo-validation>"I didn't understand this, because the configuration was exactly the same as I had in XOCE. In fact, I turned off XOA and turned on again XOCE just to test the plugin. The result was that in XOCE the plugin worked well. -
After many tries and some time of impostor syndrome we found the solution:
I don't know why, but in XOCE compiled at the beginning of november you have to configure the issuer field of the plugin with the <id-of-MSEntraID-xo-validation> (8digit-4digit-4digit-4digit-12digit).
Instead, in XOA deployed also this november, you have to set the issuer field to you XOA URL: https://<xo.company.net>/
I hope this will help, because it was a pain in the neck for us this week.
BTW: @olivierlambert this "Internal server error" coming from an uncatched exception in the plugin was not very descriptive. Even a generic try-catch block just to show in the web interface the error would help...
P.D.: I'm from Spain, so I do my best with my english

P.D. 2: Great job with all the Vates virtualization stack! You are the best!Dani
-