SAML Auth with Azure AD
-
Does it ring a bell @julien-f ?
-
For what it's worth, most Web UIs I see that take in certs use a text box/area rather than a text field which (directly or indirectly, not sure) preserves the line breaks in the cert. Everywhere I'm seeing, a text field doesn't seem to preserve the needed line breaks when its value is stored in a string.
Not sure which file(s) I'd need to edit to test a fix for this as I'm not the strongest with web development, but would be willing to try and report back.
-
Okay thanks for the feedback
 Let's see if we can fix it with a text box/area instead of a simple text field!
Let's see if we can fix it with a text box/area instead of a simple text field!Re-ping @julien-f
-
It's now fixed, please let us know if you have other issues

-
@julien-f confirmed fixed, thank you! Copy/pasted the Azure AD enterprise app's base64 cert in again and saved to get it working. After updating XO of course.
-
Yay! Great news, thanks for the feedback @dant123 !
-
@dant123
Old topic but thanks a lot for your first post, it was quite helpful for me to setup authentification with Microsoft Entra.I just didn't get immediately that you also need to specify the callback URL in the XO plugin settings, not only in the enterprise application in the Microsoft portal.
My XO is behind a reverse proxy with a Let's Encrypt certificate, but it is also working with a self-signed certificate and a local DNS record.
@olivierlambert Might be worth an addendum in the official documentation with specific screenshots for Microsoft Entra?
-
Sure, happy to have a PR on our doc!
-
Hello,
Has the saml-auth plugin updated recently ?
Using XOCE, commit c0065, it was working fine. Updating today to latest release, SAML authentication (Microsoft Entra ID), is not working anymore, I land on a page with a
'Internal server error' message.Thanks,
-
Hi,
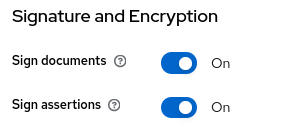
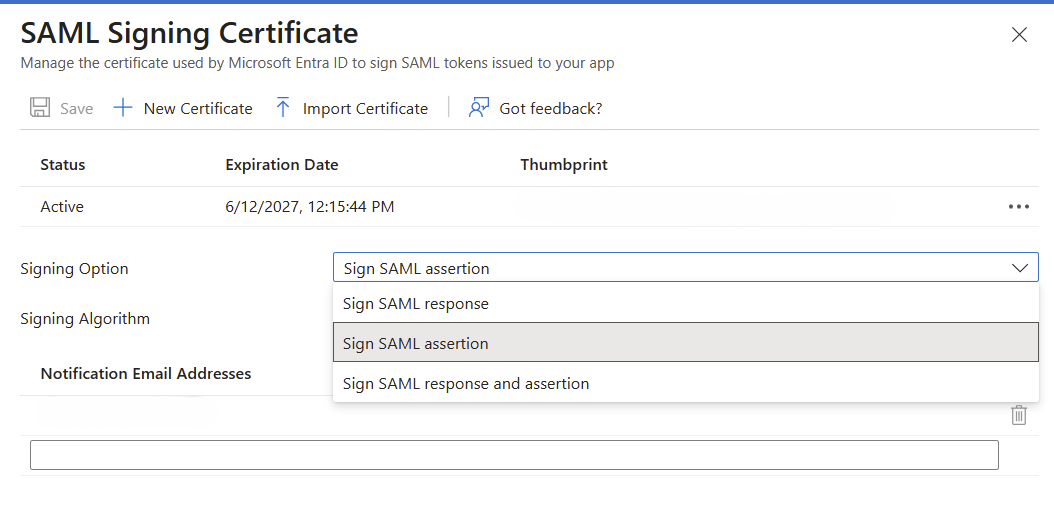
Yes it was. You need to be sure that your SAML provider used the signed SAML assertion.
Examples in Keycloak then Azure respectively:
-
@Mathieu yes indeed, I worked on this with @pierrebrunet PR https://github.com/vatesfr/xen-orchestra/pull/9042
Do you have any logs inxo-serverservice? -
@Mathieu Hi, you need to be sure to have signed assertion and signed response because only one won't be enough.
We have updated the doc when you saw the impact. Sorry for the inconvenience:
https://github.com/vatesfr/xen-orchestra/pull/9084/files#diff-6319d6b750c3bdbca61a9d9a1577a8aa4fa3a8a37764b91aef4672f69403baa4R221 -
Hello,
I've updated the cert with signed assertion and response

I also tried with a brand new certificate.
Unfortunately, login is still failing.
From xo-server:
Oct 09 08:11:17 xo-ce xo-server[272092]: Error: SAML assertion audience mismatch. Expected: 1671ff50-10e1-4a02-a0c5-4ed298898281 Received: https://XO_DNS_RECORD/ Oct 09 08:11:17 xo-ce xo-server[272092]: at /opt/xo/xo-builds/xen-orchestra-202510090759/node_modules/@node-saml/node-saml/src/saml.ts:1264:18 Oct 09 08:11:17 xo-ce xo-server[272092]: at Array.map (<anonymous>) Oct 09 08:11:17 xo-ce xo-server[272092]: at SAML.checkAudienceValidityError (/opt/xo/xo-builds/xen-orchestra-202510090759/node_modules/@node-saml/node-saml/src/saml.ts:1259:8) Oct 09 08:11:17 xo-ce xo-server[272092]: at SAML.processValidlySignedAssertionAsync (/opt/xo/xo-builds/xen-orchestra-202510090759/node_modules/@node-saml/node-saml/src/saml.ts:1151:32) Oct 09 08:11:17 xo-ce xo-server[272092]: at SAML.validatePostResponseAsync (/opt/xo/xo-builds/xen-orchestra-202510090759/node_modules/@node-saml/node-saml/src/saml.ts:808:16)And here is the plug-in configuration:
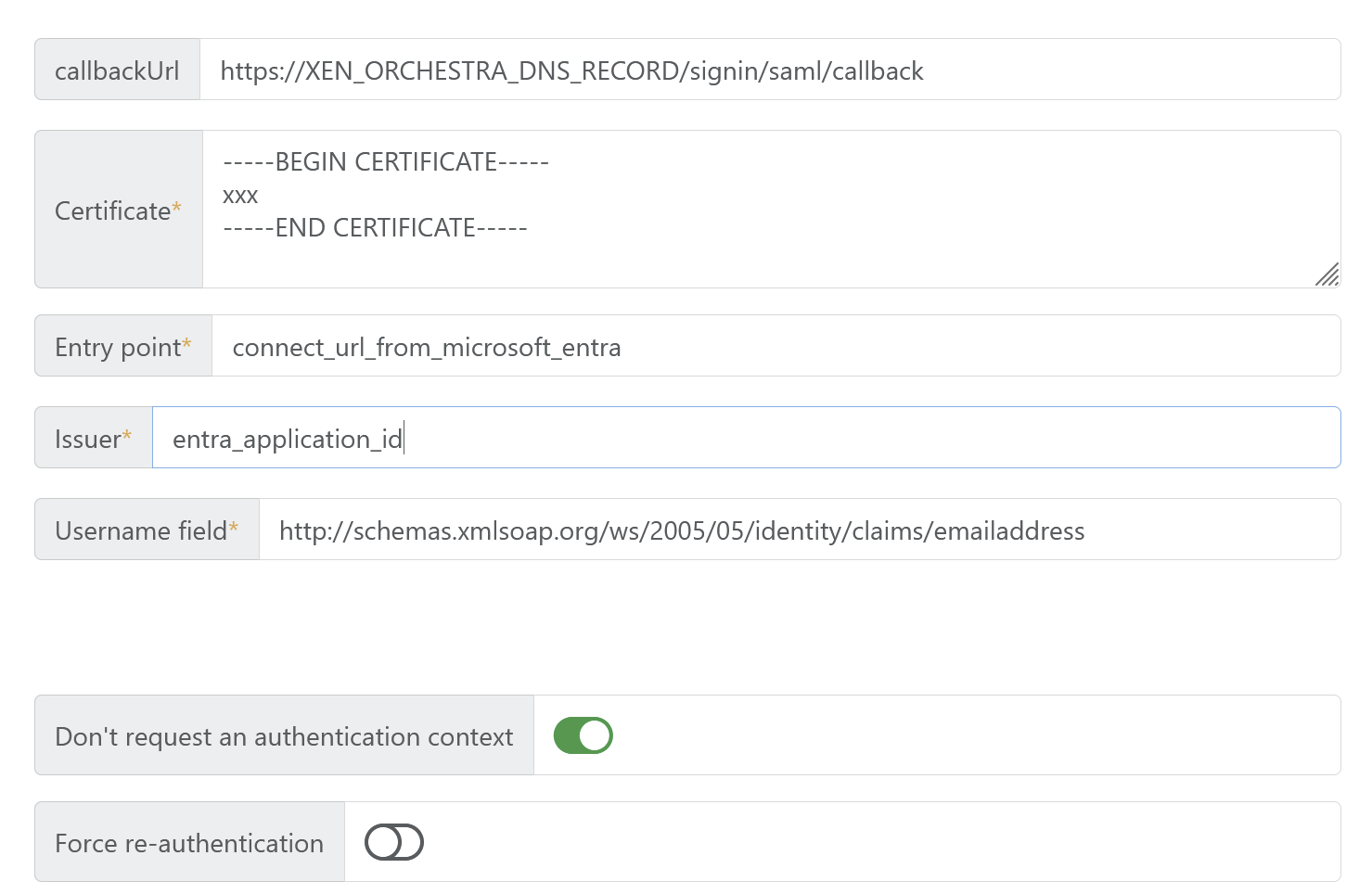
I'm not expert at all in SAML, sorry not being able to debug deeper.
-
@Mathieu Hello, can you show us your plugin configuration (without the certificate for security purpose) please?
Edit: thank you!
-
@pierrebrunet Just posted it above
-
@Mathieu Hi, do you use XO from source or do you have an XOA license? Just to know how to help you more confortably
-
@pierrebrunet
XO from source, commit 1ee07 from today. -
@Mathieu Thanks to your help, we are deploying a patch with config update and control over document and assertion signatures
https://github.com/vatesfr/xen-orchestra/pull/9093 -
@Mathieu Hi,
We merged the PR linked above with new options. If you have time, can you confirm it is working for you?
It will fix the audience error and let you choose if you want to sign responses and assertions. -
@pierrebrunet
I'm jumping in here as well. Reporting that the PR fixes it for Google Workspace as well!
However, the checkbox in GW is called "Signed response".
No further adjustments of the plugin itself was needed.
Hello! It looks like you're interested in this conversation, but you don't have an account yet.
Getting fed up of having to scroll through the same posts each visit? When you register for an account, you'll always come back to exactly where you were before, and choose to be notified of new replies (either via email, or push notification). You'll also be able to save bookmarks and upvote posts to show your appreciation to other community members.
With your input, this post could be even better 💗
Register Login