Applied latest candidate test updates to 3 x Dell OptiPlex 7040 (i7-6700, 48GB, 10Gbps-attached TrueNAS shared-storage) pool. Update process was error-free and successful. Everything appears to be working normally following the update.
Best posts made by XCP-ng-JustGreat
-
RE: XCP-ng 8.3 updates announcements and testing
-
RE: XCP-ng 8.2 updates announcements and testing
@stormi Installed all of the test updates on my three-host home-lab this weekend. Similar configuration to @gskger 3 x Dell OptiPlex 7040 SFF hosts and home-built FreeNAS server with separate physical 1Gb networks for management, storage and migration. I call it my "Tiny Cluster" due to its diminutive footprint. I use it for configuration prototyping. Intel VPRO AMT on Xen hosts and storage server enables headless console operation using MeshCommander (think poor man's iDRAC). All updates were installed without issue. Backups and restores seem to work just fine. Of special interest to me was the UEFI Secure Boot capabilities. Installed the x64 dbx.auth from uefi.org (I presume since XCP-ng is 64-bit that that was the correct choice. Probably should be made explicit in the instructions.) Seems to work perfectly. I tested with Windows 10-20H2 and Windows 10-21H1. Also tested with RHEL 8.4 which has built-in support for secure boot (Microsoft-signed bootloader shim) and that too "just works." The varstore-ls <VM-uuid> command shows PK, KEK, dbx and db in the store as expected. Stops unsigned bootloader as expected on unsupported OSes. Looks great! Thank you for all of the work you've put into it. I suspect designing and building emulated system firmware is not for the faint of heart . . .
 Very impressive!
Very impressive! -
RE: XCP-ng 8.3 updates announcements and testing
Latest version 8.3 candidate updates installed and are working fine on three-host home lab pool. Received a couple of repo errors for a certain mirror, but yum tried another mirror and it completed successfully. After updates were applied, performed live migrations between hosts with no problems and updated a Windows 11 Version 24H2 VM to the November 2024 cumulative update without problems. (VM is currently running Citrix Tools 9.3.2 without issues.)
-
RE: Mouse stops responding in XO console (XCP-ng 8.3, Win11 24H2)
Hi All. Yes, this is a very annoying problem that I've also experienced after a fresh Windows 11-24H2 install on XCP-ng 8.3 fully production-patched to date. I am accessing my Windows 11 VM console via a Windows 11-24H2 physical client PC using latest Firefox browser. The keyboard and mouse attached to my laptop via a Dell DisplayLink D3100 USB3 dock are a standard wired Logitech mouse with scroll and a wired Logitech keyboard. The XCP-ng 8.3 host is managed via XO from source (XOS) on the latest commit (66e67) as of yesterday 2/16/2025. XOS lives in an AlmaLinux 8.10 VM built with @ronivay 's superb installation script.
After some Googling around, this frozen mouse issue appears to have occurred in other hypervisors too. It looks to be a Windows problem rather than an XCP-ng 8.3/XO/QEMU problem. (I see you smiling @olivierlambert ).
I can't guarantee this technique will work for everyone, but after a day, I am no longer experiencing the mouse failure.
What appears to be happening is that the Windows Plug-and-Play (PNP) mouse driver configuration is getting borked due to multiple triggerings of PNP. During the first-boot of the VM post-installation, it finds the original emulated hardware. Following the installation of the Citrix management agent 9.4, it performs additional device configuration that doesn't always go well. In the device manager, click view, show hidden devices to see any phantom devices that I generally remove so as to keep everything as clean and pristine as possible.
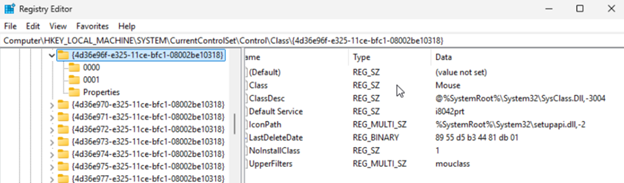
This Windows registry key: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Class{4D36E96F-E325-11CE-BFC1-08002BE10318} is your friend.
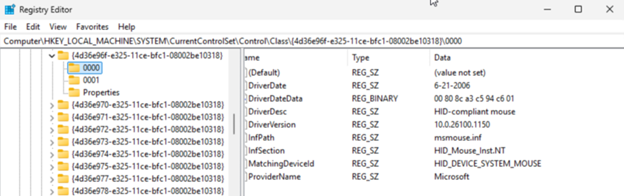
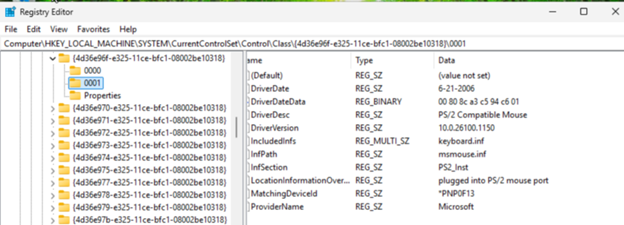
You must make sure that the value mouclass is the only value in the UpperFilters key of the above device class hive. As a general preventative against Windows oddities, I changed the value and then changed it back to mouclass to force the registry editor to rewrite the hive. You should also delete the mouse instance details folders 0000, 0001 etc. These should get deleted for you when you remove the mouse devices from the device manager. Windows will recreate those during the reboot.
Random aside: another thing I like to do is to change the VM's UEFI OVMF display settings to 1280x960 in the Tiano UEFI firmware. This allows me to see the entire VM on my 1920x1080 HD monitor when Firefox is in full-screen mode, XO console scale set to 100%, and the Windows VM display resolution also set to 1280x960. This is intended to prevent weird visual scaling anomalies.
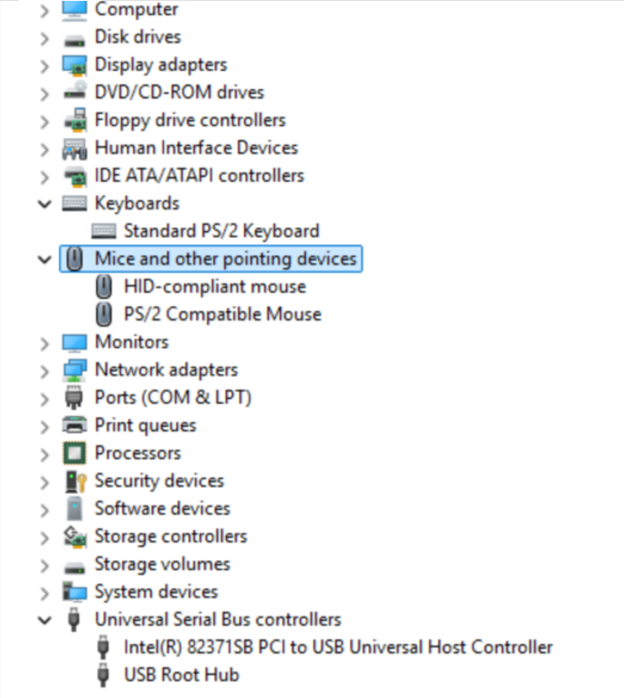
The following image is my device manager after the fix. When the mouse was malfunctioning, the system had only created the PS/2 mouse device. The HID-compliant mouse was created after deleting the original PS/2 mouse device and the failed USB Universal Host Controller devices in device manager. Following this, scan for new devices to recreate what is missing and reboot the VM so that those devices get registered and initialized correctly.
Some additional screenshots of the mouse instance registry hive values:
-
RE: XCP-ng 8.3 betas and RCs feedback 🚀
Applying the latest XCP-ng 8.3 RC2 "xen-*" and intel-microcode updates from the candidate repository worked great here as well. Everything appears to be running well.
-
RE: XCP-ng 8.3 betas and RCs feedback 🚀
Latest updates over ISO-installed 8.3 RC2 worked fine for me. I did experience one host in my three-host pool to which no VMs could be migrated. After looking at the networking from bash in DOM0, it showed that both 10G ports for the storage and migration networks were DOWN. These ports are on a genuine IBM-branded Intel X540-T2 card I bought used on eBay so it might have gone bad. Since the card has worked well for some time, I figured it couldn't hurt to re-seat it in the PCIe slot. Sure enough, that fixed it. Moral of the story: check the mundane stuff first; it's not always the fault of new updates.
-
RE: XCP-ng 8.3 betas and RCs feedback 🚀
Upgraded 3-node pool (home lab: Dell OptiPlex 7040 SFF x 3) from 8.3 RC1 to 8.3 RC2 using bootable ISO. It worked perfectly for me. As others have noted, it does ask you to select the management interface when upgrading the slave nodes. Once you do that, it automatically populates all of the previously configured network parameters for that host so you are really only confirming the existing values. The OptiPlex 7040's (i7-6700) all have Intel VPro AMT so they are running headless. The MeshCommander program is used to access the VPro console on each host. A DisplayPort display emulator dongle is needed to keep the integrated-GPU active in order to be able to see the console and firmware setup screens with this configuration. It's effectively a poor man's iDRAC. So far, everything is working well on 8.3 RC2.
-
RE: XCP-ng 8.2 updates announcements and testing
@stormi All new patches applied fine. No apparent problems identified so far.
-
RE: Refreshed XCP-ng 8.2.0 ISOs: 8.2.0-2 - testing
@beshleman I tried the latest testing update @stormi published with the updated SB support and it does indeed work properly including allowing installation of Windows Update KB4535680 on Server 2019 as previously cited. Also--a big thank you for adding the default parameter values for the improved secureboot-certs install command. Less is more. Very nice!

-
RE: Refreshed XCP-ng 8.2.0 ISOs: 8.2.0-2 - testing
@beshleman So, after yum --enablerepo=base install python-requests on each of my hosts, secureboot-certs install default default default latest works perfectly. (Cool that it installs certs to each host in the pool with one invocation from any pool host.) Interesting that it doesn't install the three files to /var/lib/uefistored until you secure boot a vm on each host. I went looking for them and was initially confused because they were only written to the pool db. Serves me right for looking under the hood!
 Looks like XCP-ng secure boot is ready for prime time. Great job!
Looks like XCP-ng secure boot is ready for prime time. Great job!
Latest posts made by XCP-ng-JustGreat
-
Citrix Releases New XenServer SDK 25.30.0 - 15-Sep-2025
Citrix just released an updated XenServer SDK with support for C, Microsoft .NET, Go, Java, PowerShell and Python. Likely useful for XCP-ng developers and users as well.
-
RE: Win11 24H2 install fails consistently
@markr All, I am currently running Windows 11 24H2 on an Intel Haswell i7-4700HQ laptop and it runs fine. What's more, it was in-place upgraded from Windows 11 23H2 using the (still working) setup.exe /product server switch compatibility bypass. (Simpler than all the LabConfig registry tweaks.) The only change I know of that simply won't run due to 24H2 is that it requires a processor capability that has been available since first generation Intel Core processors. It should run on your hardware in a VM. Seems like something else is going on.
-
RE: Pass Through of USB Storage Adapters Not Working
@JanP Thanks for the nice cookbook! I set up the passthrough SR per your instructions and then added the VUSB to the VM and started it up. As before, when I attach the disk to a USB 2.x port, I see it and it works. However, when I then plug it into a USB 3.x port and recreate the VUSB on the shutdown VM, it correctly shows USB 3.x with 10000 speed, but my Windows 11 VM does not see it. The Windows device manager shows that there is no USB 3.x device controller, only USB 2.0. Is there a way to force the emulated USB device in the VM definition to be USB 3.x? If Windows finds a USB 3.x device, it will autoconfigure it. Unfortunately, it doesn't appear to find a USB 3.x device. Just for fun, I'm running my test on a tiny Beelink EQ13 PC with Intel N100/4C,16GB/500GB SSD/2x1Gb Realtek NICs that runs XCP-ng 8.3 with 2xVMs: XOS and Windows 11 24H2. It's a $189 box I acquired in July of 2024 and I've been having a blast bending it like Gumby for different uses.
-
RE: Pass Through of USB Storage Adapters Not Working
All, I have never been able to successfully pass through a USB 3.x storage device (like a USB hard drive) to an XCP-ng 8.2/8.3 Windows VM. However, USB 2.0 devices such as a license dongle; that works. I, for one, would love to see this get fixed. FWIW, yet another "me too."
-
RE: XCP-ng 8.3 updates announcements and testing
Latest urgent updates installed on 3-node Intel pool. Everything is working as before including the pre-production code "no stats" issue, but that still resolves following xe-toolstack-restart command. Since it is currently Microsoft patch Tuesday here, the latest Windows 11-24H2 2025-05 cumulative update was installed to VM along with various Linux VM updates and live VM host migrations. All working well including latest af03c Xen Orchestra from source (XOS).
-
RE: [RHEL kernel bug] XCP vm fails to boot after newest kernel applied.
@Greg_E Maybe it only affects Intel? That would be a new wrinkle. Perhaps other AMD users can confirm if the latest AlmaLinux 8 kernel runs fine on their AMD XCP-ng 8.3 hosts? Just read the above referenced RedHat bug report here: https://access.redhat.com/solutions/7116307 Sure enough, it says Xen + Intel in problem description. Check it out.
-
RE: [RHEL kernel bug] XCP vm fails to boot after newest kernel applied.
@Greg_E Wondering what might be the difference? I am using the XenServer Linux tools version 8.4.0-1 and BIOS boot firmware.
-
RE: XCP-ng 8.3 updates announcements and testing
Latest test updates applied to 3-host Dell OptiPlex 7040 SFF (i7-6700) pool. Upgrade went smoothly and everything appears to be working normally. I did notice the flatlined stats issue mentioned previously, but the xe-toolstack-restart seemed to bring those back to life. Thanks @Greg_E and @abudef for catching and addressing that.
-
RE: [RHEL kernel bug] XCP vm fails to boot after newest kernel applied.
This is just a "me too" reply to indicate that I am also experiencing the boot failure immediately after upgrading AlmaLinux 8.10 to the latest kernel 4.18.0-553.50.1. Hopefully, the kernel fix will get integrated soon into the affected and popular RedHat 8 derivatives so that Alma and Rocky 8 et al. can continue to run on our favorite hypervisor. This is a bad one.
-
RE: Windows VMGuest changing network cause the guest to crash
@piotrlotr1 Will definitely use the trick if needed in the future. Normally, changing the network for a running VM is not something we typically need to do. Thanks!